Think back for a moment to 2003. You may recall the tragic Space Shuttle Columbia disaster, the creation of the Department of Homeland Security, or the growing hostilities in Iraq leading to Operation Iraqi Freedom. But there was also a significant event in the history of Internet security that helped to shape the current threat landscape and will continue to have an effect for years to come. I’m referring to the SQL Slammer worm, which first appeared ten years ago today.
The Slammer worm exploited a Microsoft SQL Server 2000 vulnerability that researcher David Litchfield disclosed to Microsoft in July 2002 and presented at a Black Hat security conference in October 2002 with Microsoft’s consent. Microsoft issued a security update for this vulnerability (MS02-039) in July 2002, six months prior to SQL Slammer, but the update had not been widely deployed. This was, after all, a time when many corporations were taking their first steps toward accepting the Internet, and security was often given little concern. On January 25, 2003, the first reports of a new worm began to emerge. The rapid spread of Slammer, which at 376 bytes is small enough to fit in a single tiny UDP packet, caused widespread Internet routing failures, and many corporations found their bandwidth saturated.
Other details about the Slammer worm:
- Estimates report that all vulnerable systems on the Internet were infected within 10 minutes of the release of the worm.
- The overall Internet traffic load was so great that it took down many of the largest networks and required significant cross-company cooperation and ISP participation to make networks usable again. This disruption impaired the patching process for many organizations.
- Not only did the vulnerability affect SQL Server, it also affected the Microsoft SQL Data Engine (MSDE). MSDE was included in many products from a wide range of companies, including some antivirus and security software providers.
The emergence of Slammer highlighted several glaring weaknesses in the overall state of security in 2003. Organizations quickly learned the importance of patch management, ingress firewall filtering, and incident response preparedness. While there is still room for improvement in these areas today, there’s no doubt we’re in a far better place than in 2003. Major software vendors like Microsoft have much stronger software development lifecycles and far fewer vulnerabilities in their software. The need to isolate services from the Internet and apply security updates regularly are commonly accepted best practices among most IT practitioners today.
Despite our progress, we still have a lot of work to do. As shown in Figure 1, the SQL Slammer worm is still active after ten years.
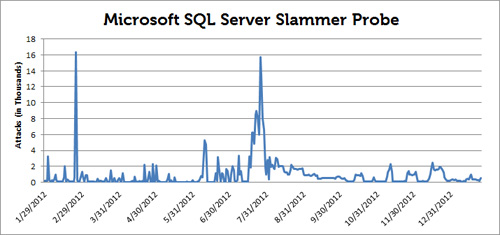
Figure 1. SQL Slammer attack activity for 2012. (Source: Dell SecureWorks)
While Slammer no longer poses the widespread threat it once did, it’s become part of the general background noise of the Internet. This trend illustrates that a vulnerable thirteen-year-old version of Microsoft SQL Server is being run on servers exposed directly to the Internet, clearly a less-than-ideal circumstance.
Just a year prior to Slammer’s emergence, Bill Gates wrote the now-famous ‘Trustworthy Computing Memo,’ refocusing Microsoft’s software development efforts with availability, security, and privacy as first-tier priorities. Slammer emphasized the importance of this message. In the decade since the memo, Microsoft’s track record on security has significantly improved, and security is a foremost concern of most organizations. The threat landscape has shifted to focus more heavily on client-side attacks, browser plugins, and common file formats, but it’s important to remember our history. At global Internet-scale, forward motion beyond the threats of yesterday can take decades as we continue to surge forward into new areas of technology.
Secureworks has been acquired by Sophos. To view all new blogs, including those on threat intelligence from the Counter Threat Unit, visit: https://news.sophos.com/en-us/.

