Android security
The rapid evolution of threats targeting the Android mobile platform continued in Q2 2012. Malicious actors are beginning to use variations of existing attacks, which have historically been successful on traditional computers. Hybrid attacks are emerging that combine traditional computer and mobile threats. While the majority of Android malware is still found in unofficial third-party markets, attackers are increasingly leveraging drive-by downloads, luring victims to malicious sites using in-app advertising links, social networking profile pages, and email-borne campaigns. Similarly, recent malware uses Twitter for command and control (C2) communication. Perhaps most concerning is the high frequency of mobile malware families that use rooting (also known as jailbreaking) privilege escalation exploits. These exploits effectively grant more administrative access to malware than a typical user or device management software has.
In application update attacks, a user first downloads a malware-free application that was created by an attacker. At some point, the original application is updated to one that contains malicious content. Android can permit installed applications to automatically update if the updated application requests the same application-level permissions (such as "Internet" or "send SMS") and is cryptographically signed by the same key as the incumbent application. Security researchers who download the original application will not observe the malicious content unless the application is updated as part of the research process. For instance, the DroidKungFu malware first observed in Q4 2011 is downloaded from an alternative marketplace as a benign virtual private network (VPN) application. However, when the application is updated on the mobile device, malware is installed as part of the update. In the future, these attacks may escalate to the point where a second automatic update is used to replace the malicious application with a benign application, further complicating detection.
As in Q1 2012, Android security continues to suffer from privacy and implementation issues related to software added by manufacturers and carriers, such as the privacy and security issues revolving around CarrierIQ and HTC's poorly implemented logging software. Similarly, modifications made by manufacturer ZTE to the Score M smartphone in May 2012 included a vulnerability permitting full root access to the device.
The ubiquity of mobile devices and the regularity with which they move between networks challenge conventional security boundaries. A new threat in the second quarter, dubbed NotCompatible after one of the C2 domains, acts as a proxy that gives the attacker access to networks accessible by the mobile device. As shown in Figure 1, this Android malware poses as a security update and is downloaded directly from the Internet. Once executed, the malware behaves as a botnet client, initiating contact with C2 servers and executing attacker commands. The connectProxy command permits the attacker to make TCP connections through the device, including connections to any local or restricted hosts accessible by the device. In the figure, the remote attacker is shown establishing connections to a private server through a device connected to corporate Wi-Fi network. The remote attacker may also connect to a public service via the mobile device, which creates additional risk and liability to the user. To the service (which could be any accessible service, such as websites distributing malware, file sharing sites, popular social networking sites, etc.), the mobile user (not the attacker) will appear to be the source of communication.
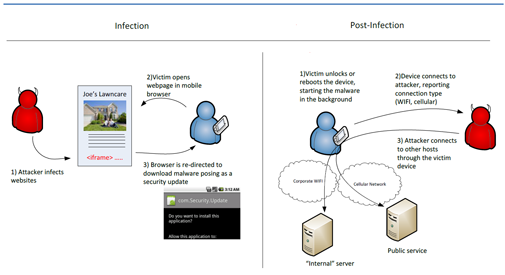
Figure 1. Android NotCompatible malware infection process and post-infection proxy diagrams. Click image to enlarge. (Source: Dell SecureWorks)
Apple iOS security
While Android persists as the primary target for malware, multiple exploits for the Apple iOS have been developed with the intention of enabling Apple iPhone or tablet owners to control (or jailbreak) their iOS devices, and device owners are using the exploits for this purpose. These exploits, commonly found on jailbreaking websites, can give Apple device owners elevated administrative access on their devices. A user wanting to jailbreak his iOS device willingly downloads an application-level exploit (such as a browser or PDF-based exploit) followed by a root privilege escalation exploit. The security posture of a jailbroken iOS device is often unknown because determining the posture may require extensive analysis of the exploits. Currently, public exploits designed to enable users to jailbreak iOS devices are available for all iOS phones and tablets. Although the current iOS exploits have been designed for use by Apple phone and tablet owners, there is nothing to prevent these same exploits from being used by attackers looking to compromise a device and the data it can access.
In May 2012, Apple released a document simply titled iOS Security. The document combines security-relevant information previously fragmented across several developer and administration documents. This iOS security guide does not clearly indicate which versions of devices and operating systems employ each part of the security architecture, but the existence of the document does increase the transparency of iOS security.
Summary
Security questions and issues persist across mobile device platforms. Rapid development of threats targeting the Google Android platform continued in Q2 2012 as attackers employed clever direct and indirect strategies to place malware on devices. Recent threats such as NotCompatible serve as actual implementations of what was at one time considered a "theoretical attack." The Dell SecureWorks Counter Threat Unit (CTU) research team expects similar continued development of new exploit tactics on the Apple iOS platform. However, Android's relative transparency and Apple's recent iOS security guide represent steps toward illuminating various security features and capabilities on these devices. Decision makers must be informed of current device management capabilities and mobile application marketplace policies, but must also be aware of the ever-evolving mobile threatscape.
Secureworks has been acquired by Sophos. To view all new blogs, including those on threat intelligence from the Counter Threat Unit, visit: https://news.sophos.com/en-us/.

