The Unnamed Police Department (we'll just call them the UPD for short) is charged with keeping the peace in a major American metropolitan area. For a public safety website, theirs is quite advanced. Visitors can view dynamically generated maps showing the distribution of different classes of crimes, make anonymous tips to the narcotics squad, and even try to sign up to join the force. As those of us that work in information security well know, all that rich web functionality brings increased risk.
This past Thursday afternoon I received a report from a colleague that the UPD public website appeared to be serving up malicious JavaScript injections. The URLs of the injected scripts were consistent with the recent waves of mass SQL injection attacks that have targeted Microsoft IIS sites backed by Microsoft SQL Server databases. The injected JavaScript payloads were consistent with malicious scripts generated using the Neosploit obfuscation tool. The first stage script redirected victims to another script, this one hosted at a domain name registered just the day before with a German domain registrar.
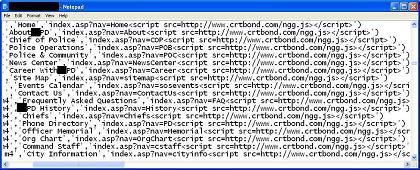
The impact of all this? Visitors to the UPD website were having their web browsers loaded with a witches brew of exploits, potentially leading to complete system compromise. While not all visitors were successfully exploited, enough folks are getting owned with these attacks to make them increasingly popular with the bad guys. Users of a tool such as the NoScript extension for Firefox (or possibly Microsoft's new XSSFilter being included with Internet Explorer 8) would have been protected.
I immediately contacted the UPD and reported the issue. The conversation was initially pretty humorous, as you might imagine. Fortunately, the department includes a cybercrimes unit and my report was immediately routed to them. The contact at the UPD called me back about 5 minutes later and informed me one of the investigators in the cybercrimes unit had indeed confirmed the problem, and that they were working to resolve the issue. To verify the report, the cybercrimes investigator supposedly browsed to the UPD's own public website and saw his anti-virus software light up with warnings.
I checked back less than four hours later, and the site appeared clean. I'm impressed with the speed of the response, given previously reported compromises of state and local government websites (credit to Sunbelt Blog: here, here, here, and here). I really thought I had enough time to get home before writing a cron job to keep checking the site for when it got cleaned up!
Unless the underlying SQL injection vulnerability was fixed however, this site is very likely to fall victim again, and soon.
Secureworks has been acquired by Sophos. To view all new blogs, including those on threat intelligence from the Counter Threat Unit, visit: https://news.sophos.com/en-us/.

