
Beijing, China 4/2008
Zhong guo hei ke tan hei ke, or "Chinese Hackers Talk Hacker", was an information security conference held earlier this year in Beijing, China. Sponsored by Yesky, a popular Chinese electronics e-retailer, the event drew around 80 attendees, most of which were hackers that had previously communicated entirely over the Internet. Some of the more well-known attendees included Frankie Zie (now CTO of a network security company in China, former black-hat and well-known in Shenzen), r00t (has hacked numerous U.S. websites), and netcc (claims to possess the ability to hack a thousand websites per month).
These figures show some attack trends gathered by the SecureWorks CTU (Counter Threat Unit). Shown here is number of cyber-attacks per foreign country. These stats are from September 2008, however it is clear China's numbers dwarf other foreign countries, and still, attacks from China continue to increase.
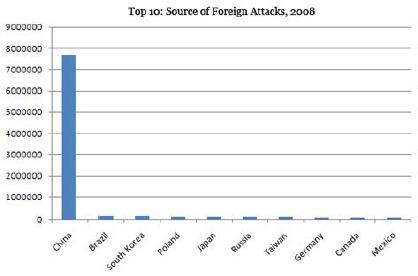
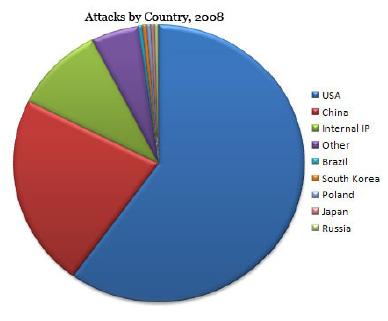
In interviews given at the conference and online, we get some insight into the Chinese hacking subculture and how it is growing at such a rapid pace. Translated below are some interesting responses that seemed to reflect the attitude of the populace:
Q: Under what circumstances will you perform a hack?
A: If it is a matter that affects us internationally, then we will gather members to perform the attack. Most of the time, we attack through the web site.
Q: What's the difference between Chinese and U.S. hackers?
A: Over the past few years, Chinese hackers could not compare with hackers overseas. However, our hacking level is increasing rapidly. For example, we recently discovered a Microsoft vulnerability.
Xiao Rong, well known among the guests, provides software tools for use by other members of the hacking community. He begins his work nightly at 9pm, and spends all night scanning overseas websites for latent vulnerabilities. His guiding principle is 'Don't be hostile towards society.' Overall, the attitude seems to be white-hat in nature, despite some guests' history. It seems that if one's intentions are judged to be 'good,' performing the hack seems to be acceptable (never mind the legalities).
Here's more from the conference:
Q: What is a hacker?
A: Hackers are a very disagreeable topic. In my opinion, hackers are interested in any kind of computer system, they proactively look for vulnerabilities in systems and at the same time look for solutions. Another kind of hacker, the 'cracker,' just intentionally break into others' systems and cause interruption to their systems. Now, the media categorizes both hackers and crackers alike. I must clarify that this is wrong.
Q: Who is your idol?
A: Kevin Mitnick. In my opinion, the real hacker will not name himself as such, only by others.
Q: What does the existence of hackers mean for the Internet?
A: The internet would not exist without hacker culture. In the 70's, hackers proposed a simple machine to serve people, and thus created the PC. Apple was also created by 70's hackers. Later, hackers proposed the sharing of information and thus created the Internet.
Another guest known as 'Shot Gun' commented: "More than 80 percent of Chinese websites are vulnerable. In February of this year, the most secure network, Yahoo, was hacked. This made people realize the importance of network security. However, many companies don't have the resources to secure their own network."
Later, while speaking about what 'real hacking' involves:
"The true hacker will lock themselves in a room, eating only instant noodles, with cigarette butts everywhere. The men do not shave for months, just to solve a technical difficulty."
"Hackers are irreplaceable. Hackers are warriors, we should be grateful for their dedication and give them a 'real name.'"
As the Chinese 'hackers' and 'crackers' (it's not immediately apparent that white-hats in other nations are playing by the same rules either) continue to mount attacks, the Dell SecureWorks CTU continues to investigate and protect against these threats.
Information Source: http://blog.54master.com/index.php/710520/viewspace-31153
Secureworks has been acquired by Sophos. To view all new blogs, including those on threat intelligence from the Counter Threat Unit, visit: https://news.sophos.com/en-us/.

