Dell SecureWorks Counter Threat Unit™ (CTU) researchers have observed the distribution of a modified version of the Gameover Zeus malware. The global Gameover Zeus infrastructure was disrupted in late May 2014 by law enforcement and private industry partners during Operation Tovar. The infrastructure, including its peer-to-peer (P2P) network, remains under the control of those organizations and is not available to the threat actors who originally operated it. The new version has jettisoned the P2P component in favor of a centralized command and control (C2) infrastructure that is based on a previously unseen domain generation algorithm (DGA).
CTU researchers observed this latest version of the Gameover Zeus malware at approximately 10:00 am EDT on July 10, 2014 in a spam email sent by the Cutwail botnet (see Figure 1). Other lures containing the same malware were also observed around that time.
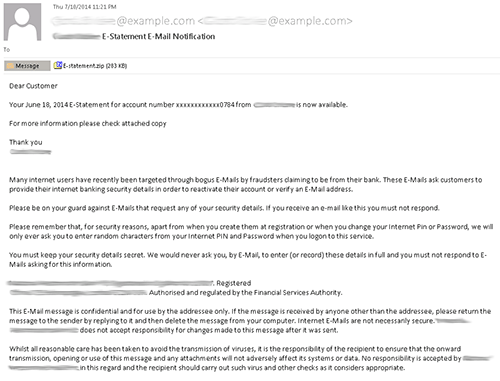
Figure 1. Cutwail botnet spam email containing the new Gameover Zeus variant. (Source: Dell SecureWorks)
Opening the attached ZIP archive reveals a malicious file named "E-statement.pdf.scr" (MD5: 5e5e46145409fb4a5c8a004217eef836) that displays a familiar Adobe Reader PDF icon. When executed, the malicious file creates a modified copy of itself inside a directory under %AppData% or %Temp%. Both the filename and directory name are random; for example, Beexfkaaj.exe, Keebzaityli.exe, and Koumygubwoi.exe. Stolen data is stored in %AppData% as a file with another randomly generated name and extension, such as xiip.obm, veok.ywg, and aveh.bir.
The malware iterates through a list of potential C2 servers created by an internal DGA. Previous Gameover Zeus versions relied primarily on the P2P component for communication but reverted to a DGA if no peers could be contacted. The new DGA used in this version generates 1,000 domains per day. Each domain name contains 21 to 28 lowercase alphanumeric characters under the .com, .net, .biz, and .org top-level domains (TLDs). For example:
- bmo0ve7lxujkiid9sycsfxb.biz
- 1gkdng316lekt41ohkj3yi1gxzt.net
- 1x162cb489ebmyfibcyujrg7.com
- 1m29d4pp9t4t910tf4htihifak.org
- 1odurmg100mx3pojsrt51d95f0o.com
When the malware successfully contacts a live C2 server, the malware sends RSA-encrypted data using an HTTP POST request on TCP port 80 (see Figure 2). The use of RSA ensures bots can communicate only with attacker-controlled assets.
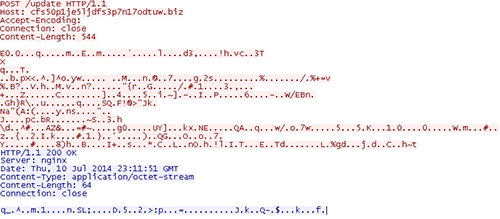
Figure 2. Gameover Zeus phone-home traffic over HTTP. (Source: Dell SecureWorks)
The C2 servers observed as of this publication are hosted on a separate proxy botnet that uses a double fast-flux DNS configuration. This botnet, which is operated and rented out by a different threat group than the one operating this Gameover Zeus variant, has been used by dozens of malware families over the past year, including Rerdom, KINS, Pony Loader, and Andromeda. It typically includes several hundred to several thousand hosts at a time, mostly located in Russia and Ukraine.
At approximately midnight EDT, July 11, 2014, CTU researchers sinkholed one of the domains generated by the Gameover Zeus DGA. In the twelve hours following, the domain was contacted by 177 active compromised systems. Table 1 shows the geographic distribution of these compromised systems.
| Country | Number of systems |
| United States | 32 |
| India | 32 |
| Singapore | 25 |
| South Korea | 8 |
| Turkey | 8 |
| Great Britain | 7 |
| Italy | 5 |
| Greece | 4 |
| Malaysia | 3 |
| Spain | 3 |
Table 1. Geographic distribution of systems compromised with latest Gameover Zeus variant.
To mitigate exposure to this threat, CTU researchers recommend that organizations use available controls to restrict access using the indicators in Table 2. The domain in the indicators table may contain malicious content, so consider the risks before opening it in a browser.
| Indicator | Type | Context |
| cfs50p1je5ljdfs3p7n17odtuw.biz | Domain name | C2 server |
| ce025e2973ce384f651bd4bbbc1698e9 | MD5 hash | Malware sample |
| 6c8a03895665575619a6193d342cdc79500680971ff4398c62a2d6e84188f49a | SHA256 hash | Malware sample |
| 5e5e46145409fb4a5c8a004217eef836 | MD5 hash | Malware sample |
| 3ff49706e78067613aa1dcf0174968963b17f15e9a6bc54396a9f233d382d0e6 | SHA256 hash | Malware sample |
| 03ac662ba5bdf3e9ab3c398da37e5439 | MD5 hash | Malware sample |
| ddc013410b944092c1eeb39699504dbfc6a90146632c93b0a6085b16aa65e802 | SHA256 hash | Malware sample |
| 30bd87b5b1a4c151662e32ca0edd658b | MD5 hash | Cutwail spam attachment (E-statement.zip) |
| 30e2024f544fe8d904502cafd614d1fbfb30d428367a23757f2639dee0aa3cc6 | SHA256 hash | Cutwail spam attachment (E-statement.zip) |
Table 2. Indicators for the Gameover Zeus malware variant.
Secureworks has been acquired by Sophos. To view all new blogs, including those on threat intelligence from the Counter Threat Unit, visit: https://news.sophos.com/en-us/.

