
Figure 1. Cartoon about Internet identity published in The New Yorker. (Source: Peter Steiner The New Yorker Collection/The Cartoon Bank)
Trust and identity on the Internet are ongoing issues. As far back as 1993, The New Yorker magazine published its now infamous cartoon, “On the Internet, nobody knows you're a dog.” Governments, enterprises, and individuals alike continue to wrestle with associating “real” identity with various forms of “digital” identity.
Identity is rarely verified; instead, it tends to be supported through context. That context may involve building up a single consistent “known” persona, or building a social graph on a social networking platform to develop a “socially validated” identity (see Figure 2a).
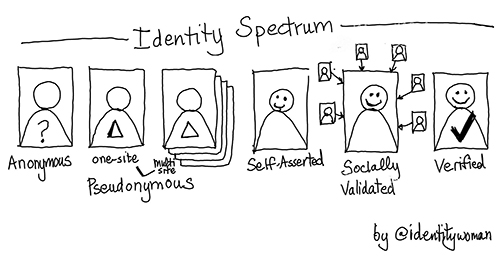
Figure 2. The Identity Spectrum. (Source: http://www.identitywoman.net/the-identity-spectrum)
The U.S. government showed insight in 2010 with its draft proposal for the National Strategy for Trusted Identities in Cyberspace (NSTIC), and verification solutions do exist. However, the widespread adoption of such solutions hasn't occurred. Indeed, misuse of social media in this regard is on the rise and is even the subject of mainstream entertainment programs like MTV's Catfish: The TV Show.
That said, lack of identity on the Internet can be a good thing; for example, allowing people living under oppressive regimes a dissenting voice they couldn't hope to bring to the real world. But what happens when a threat group uses those tactics to further its goals?
Recently, Dell SecureWorks Counter Threat Unit™ (CTU) researchers uncovered a set of fake profiles supporting a suspected Iran-based threat group's cyber operations and documented the findings in “Suspected Iran-Based Hacker Group Creates Network of Fake LinkedIn Profiles.” Fake profiles with fake photos and fake supporting social graphs, some that even changed identity and affiliation while CTU researchers were investigating…these are the catfish of the cybersecurity realm.
Secureworks has been acquired by Sophos. To view all new blogs, including those on threat intelligence from the Counter Threat Unit, visit: https://news.sophos.com/en-us/.

