Organizations should consider endpoint solutions as part of a comprehensive security program, and maximum effectiveness requires implementation prior to an incident occurring.
Most organizations will experience a data breach at some point, and their response can affect the organization's future. Without proper instrumentation and visibility at the endpoint, it is more difficult to detect an adversary and react effectively to contain the threat. Three key factors influence the outcome of a security incident: the ability to detect a targeted adversary, the visibility to determine what the adversary achieved, and the agility to contain the threat. If an organization cannot adequately address these factors, then an unsophisticated adversary with limited initial access can become a significant threat to the overall network infrastructure.
In September 2016, SecureWorks® Incident Response (IR) analysts investigated a breach where an adversary gained access to an application server that allowed Terminal Services connections directly from the Internet. Use of Advanced Endpoint Threat Detection (AETD) - Red Cloak™ helped the SecureWorks analysts detect, contain, and evict the adversary before the client experienced data theft or reputational damage.
Detection
The client became aware of the incident when users accessing the application server complained to the client's IT staff that the application was running slowly and at some points was unresponsive. The IT staff examined the system and determined that several suspicious programs were executing. The client contacted SecureWorks, and an initial investigation revealed that the suspicious programs included click-fraud malware, Bitcoin-mining software, and batch scripts (see Figure 1). The initial investigation also identified the account (one with domain administrator privileges) responsible for executing the programs, but could not determine the origin and length of time the binaries had been present on the system.
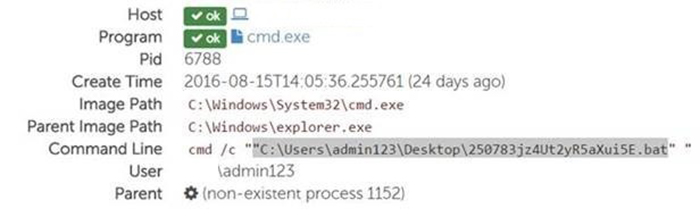
Figure 1. Execution of batch script on compromised system. (Source: SecureWorks)
Investigation
SecureWorks IR analysts used AETD Red Cloak to help determine the overall scope of the incident and identify affected systems. Digital forensic analysis of system images determined that the system that had been the original point of entry was compromised 24 days before the incident was detected. The adversary had used brute-force attempts against available Terminal Services accounts to guess the password for the domain administrator account.
Digital forensic analysis of the compromised system did not show any obvious signs of lateral movement. Examining a single system does not provide sufficient context to determine if a threat is contained because it contains a limited number of artifacts, many of which may be quickly overwritten. Based on information from the client, IR analysts determined that the compromised domain administrator account was old and should not have been used by client administrators, contractors, or internal employees. If endpoint visibility or central logging had not been in place prior to the incident, forensics of the single system would be the best approach. However, the IR analysts were able to use process creation data from the endpoint service to quickly search the network for use of this account for the previous 30 days, including data captured prior to the compromise. The search revealed that the compromised domain administrator account was used exclusively on the compromised system and had not been used to move laterally to other systems in the network. While traditional log analysis of a central source could have resulted in the same answer, the data is often archived in a way that makes searching the data extremely time consuming and slows the investigation and containment efforts. Endpoint solutions increase the speed at which an analyst can review a large amount of data across many systems in the network. The gap in time between these two methods is often the difference between an adversary moving deeper into the network or being completely contained.
Conclusion
If an adversary's actions are unknown, particularly in a domain administrator compromise, rebuilding the domain is often the best and only way to fully recover. Rebuilding a domain infrastructure is a time-consuming and costly (in terms of both money and business resources) process. Deploying an endpoint monitoring service as part of a proactive detection plan can detect and identify malicious activity before it can expand. As a result of the available Red Cloak data, SecureWorks analysts were able to determine with a high degree of confidence that the adversary did not move to other systems within the network, eliminating the need to rebuild the entire domain. The observed activity indicates that the adversary was opportunistic and focused on monetization. It is likely that over time the adversary would have identified their access level and pivoted elsewhere, or a second threat actor would have discovered the publicly accessible server and caused an even bigger incident.
Secureworks has been acquired by Sophos. To view all new blogs, including those on threat intelligence from the Counter Threat Unit, visit: https://news.sophos.com/en-us/.

