Attackers typically rely on large botnets to generate distributed denial of service (DDoS) traffic; however, there are additional ways to amplify attack traffic. The DNS amplification attack is a popular form of DDoS that relies on exploitation of publicly accessible open DNS servers to deluge victims with DNS response traffic.
In DNS amplification, the attacker crafts a small DNS message, usually 60-80 bytes, with a victim's spoofed IP address and sends it to an open DNS resolver to trigger a response DNS message back to the victim's address. The response is usually 2000-3000 bytes, an amplification factor that is approximately 60 times the original value. This amplification can significantly increase the volume of traffic that the victim receives.
An attacker typically conducts DNS amplification by sending DNS requests of type "ANY" (see Figure 1). This type of request returns all known information about the DNS zone, which allows for the maximum level of response amplification directed to the victim's server.
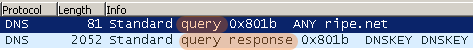
Figure 1. DNS amplification example. (Source: Dell SecureWorks)
In 2006, early research (PDF) into DNS amplification by Randal Vaughn and Gadi Evron described an attack on Sharktech Networks that exploited 140,000 name servers to generate DDoS traffic as high as 10Gbps. In 2013, we are seeing attacks based on a similar technique exploiting 30,000 unique open DNS resolvers and reaching 300Gbps. Generating this type of DDoS attack would only require the attacker to generate approximately 3Gbps of traffic, which can be accomplished by using a small botnet (see Figure 2) or even by exploiting legitimate cloud services.

Figure 2. DNS amplification attack using a botnet. (Source: Dell SecureWorks)
The Open Resolver Project was developed to shed light on the issue of publicly open DNS resolvers exploitable over the Internet. As of August 2013, the project has compiled a list of more than 33 million resolvers that respond to DNS requests, with 28 million resolvers that are marked exploitable.
Dell SecureWorks Counter Threat Unit™ (CTU) researchers gathered and analyzed the Open Resolver Project dataset and correlated 33 million IP addresses with their geographic location and network owners. The following countries had the highest percentage of active open resolvers:
- China (9.5%)
- United States (6.6%)
- Taiwan (5.4%)
- Mexico (5%)
- Vietnam (4.7%)
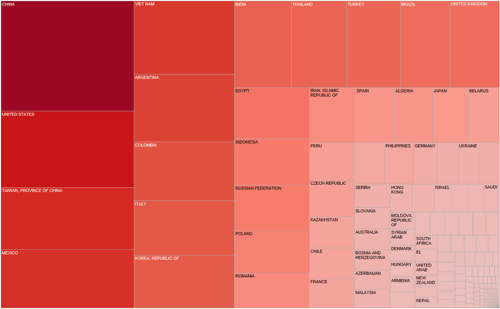
Figure 3. Distribution of open resolvers by country. The larger the cell and deeper the color, the more open resolvers. (Source: Dell SecureWorks)
Because DNS amplification is based on an attacker's ability to send DNS requests with spoofed IP addresses, ISPs are advised to drop any DNS traffic with spoofed IP addresses. The document "Network Ingress Filtering: Defeating Denial of Service Attacks which employ IP Source Address Spoofing" describes best practices for implementing ingress traffic filtering to restrict DDoS attacks that rely on forged IP addresses. Making these changes would considerably reduce the DDoS threat from DNS amplification.
Other effective remediation involves reducing the number of insecure recursive open resolvers. Administrators should check for open resolvers in their public networks by using the search feature on the Open Resolver Project website. If DNS servers in your public network provide open-recursion, strongly consider disabling it and only accepting recursive DNS requests from trusted sources. Additional details on DNS amplification attacks and mitigation techniques are provided in the Dell SecureWorks analysis "DNS Amplification Variation Used in Recent DDoS Attacks" and in US-CERT alert TA13-088A.
Secureworks has been acquired by Sophos. To view all new blogs, including those on threat intelligence from the Counter Threat Unit, visit: https://news.sophos.com/en-us/.

