On March 27, 2020, the U.S. government approved a $2 trillion USD stimulus package that provides COVID-19 (also known as coronavirus) pandemic relief for qualified taxpayers in the form of $1,200 checks. Since then, Secureworks® Counter Threat Unit™ (CTU) researchers have observed an increase in tax identity theft aimed at fraudulently obtaining stimulus checks (see Figure 1).
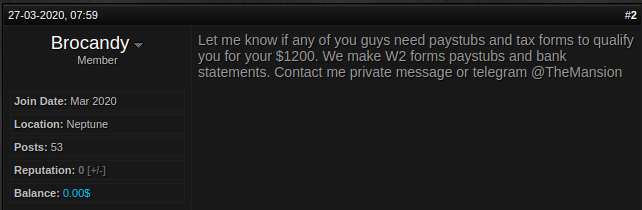
Figure 1. Advertisement of tax documents to steal stimulus checks. (Source: Secureworks)
In another underground forum post, an English-speaking threat actor known as “DoctorZempf” claimed to have found information by searching tax preparers’ trash dumpsters. Cybercriminals could use taxpayer information to steal identities and apply for a victim’s stimulus relief check. Other discarded data could allow threat actors to impersonate the tax preparers in a social engineering campaign against their customers.
In April, the stimulus checks were sent to individuals who filed U.S. federal taxes in 2019 and 2020 and met the stimulus requirements. Some checks were sent to deceased citizens, providing opportunities for threat actors. A cybercriminal possessing a deceased individual’s data (e.g., personal information (fullz), paystubs, bank account details, individual taxpayer identification number (ITIN)) could file a fraudulent tax return for the victim and claim an applicable stimulus payment and tax refund.
CTU™ researchers have observed cybercriminals discussing the success of coronavirus stimulus fraud attempts and soliciting partners to share resources (see Figure 2).

Figure 2. Threat actor seeking a partner for stimulus fraud. (Source: Secureworks)
CTU researchers also observed threat actors using phishing pages disguised as Internal Revenue Service (IRS) tax forms required for stimulus checks. The threat actor can use the submitted information to impersonate the victim on IRS tax forms and obtain the victim’s tax return and stimulus check (see Figure 3).
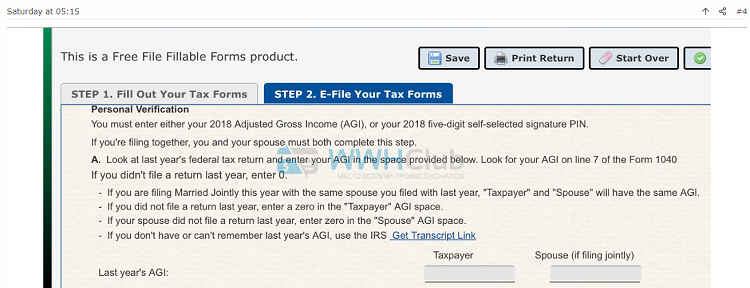
Figure 3. Phishing page to collect victims’ tax information. (Source: Secureworks)
Threat actors are selling data packages that simplify the tax identity theft process (see Figure 4).
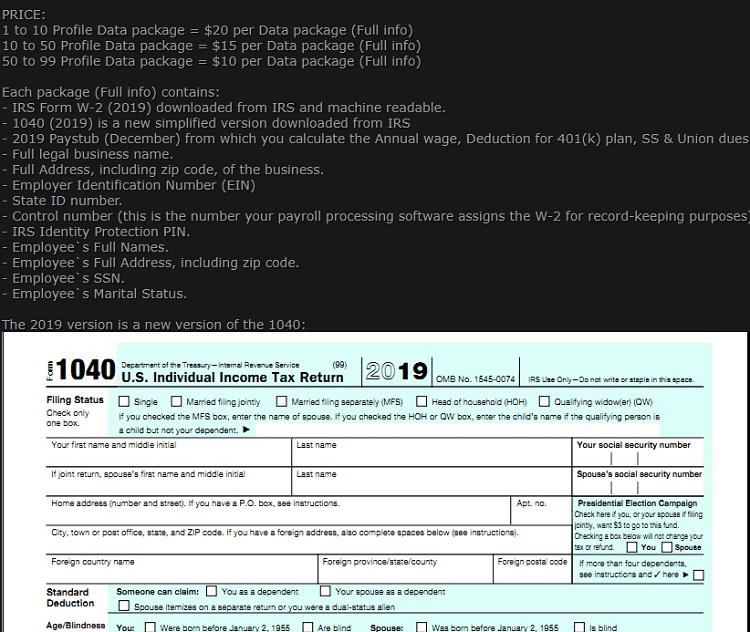
Figure 4. Advertisement of tax profile data packages used for IRS stimulus fraud. (Source: Secureworks)
Some cybercriminals directly collect the victims’ data via phishing pages or social engineering, while others purchase databases of fullz and account information advertised on underground forums. Figure 5 advertises an auction for a database that could allow a buyer to create 40,000 more tax profile data packages.
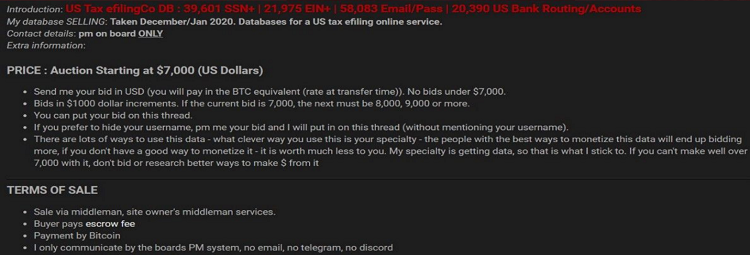
Figure 5. U.S. tax e-filing services company database offered for sale and later sold. (Source: Secureworks)
The IRS posted sample phishing emails on its website for individuals who are unsure if an email is legitimate. The IRS does not initiate taxpayer communication through email and encourages recipients to report these emails.
CTU researchers recommend that clients implement best practices that can deter stimulus fraud as well as other tax scams that impersonate the IRS and attempt to steal W-2 information. Victims of identity theft should also immediately report the incident to the IRS and a credit agency to limit damage.
- Implement multi-factor authentication for Internet-facing resources that store financial information, personally identifiable information (PII), and corporate or personal email addresses.
- Protect customer data with up-to-date secure encryption.
- Train employees to recognize and report phishing attempts that use email or malicious advertisements to try to steal sensitive information.
- Institute processes to verify the legitimacy of requests for PII, financial information, or account updates by using previously established out-of-band channels such as telephone.
- Dispose of sensitive information securely (e.g., shredding paper documents).
Secureworks has been acquired by Sophos. To view all new blogs, including those on threat intelligence from the Counter Threat Unit, visit: https://news.sophos.com/en-us/.

