Assess Your Risk From an Advanced Persistent Threat Attack
Understanding the true threat your organization faces from an Advanced Persistent Threat (APT) represents half the battle to effectively defending against it. To do so, you first need to know what makes your organization attractive as a target. You then need to develop a strategy or vision for how your organization will adapt to counter the threat.
If you missed it, be sure to check out part A of this series on the ABCs of APTS, where we demystify the ‘threat’ in Advanced Persistent Threats.
- Understand the 'Threat' in Advanced Persistent Threats
- Assess Your Risk
- Learn What You Can Do to Protect, Detect and Respond
Are you at risk?
Should you be concerned about Advanced Persistent Threat (APT) actors targeting your business or organization?
Use the four-phase process below to determine if your organization is at risk and if so, how you can develop a roadmap to achieve "heightened security resiliency" against Advanced Persistent Threats. This process can also be applied to less sophisticated but targeted threat actors such as hacktivists and cybercriminals.
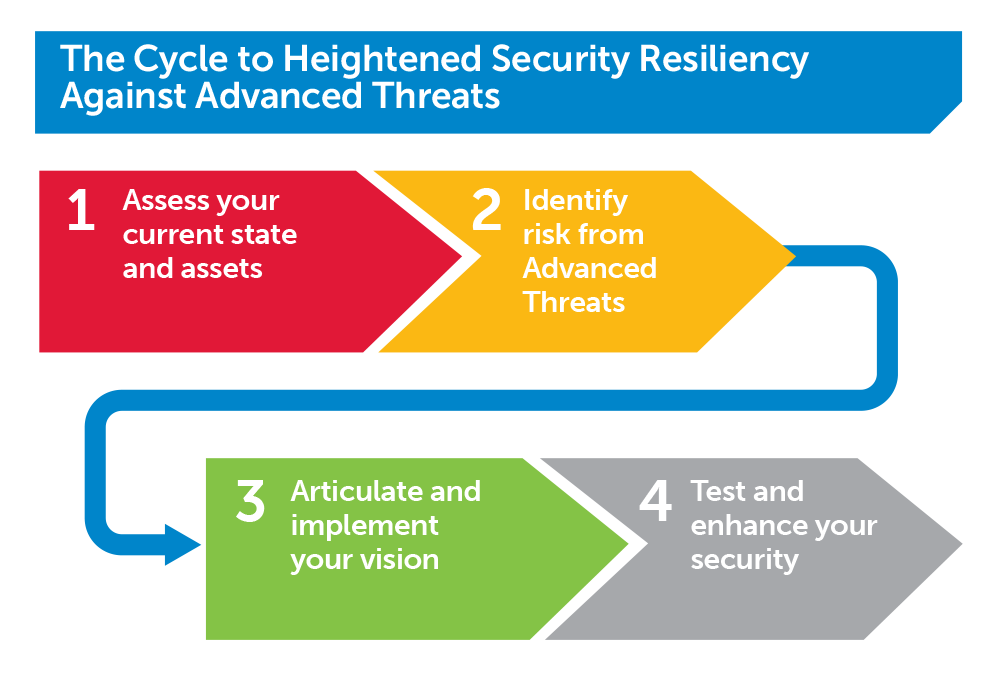
The Cycle to Heightened Security Resiliency Against Advanced Threats represents a continuous process whereby organizations periodically reassess their current state, identify their risk from Advanced Threats including APT, reshape their vision or strategy as needed, and finally test and incorporate new learnings.
Is your organization likely to be targeted by APT actors?
The fact is that many organizations have a low risk of attack from an APT actor.
However, it is imperative that organizations conduct a thorough assessment of their current state and map learnings to what we know about Advanced Persistent Threats to determine the real likelihood or risk of attack (Phase 1 and Phase 2).
For organizations where there is a greater risk of attack by an APT actor, security leadership will need to proactively implement a revised security vision Phase 3) that works to address the questions below:
- How do I protect my organization and its assets?
- What organized elements may be targeting our organization?
- How can we detect Advanced Persistent Threats when they strike?
- How do we determine if our organization has already been compromised?
- How vigilant are our employees to the types of methods APT actors may use?
Given the relative sophistication and persistence of APT actors, testing of security capabilities and policies is critical to promote continuous improvement (Phase 4). This entire process should be repeated on a periodic basis.
Phase One: Assess Current State and Assets
This phase involves identifying what may make your organization attractive to an Advanced Persistent Threat (APT) actor. In addition, this phase involves assessing your current security policies, capabilities and posture.
For all of the areas below, we recommend an honest and thorough review of security practices and policies currently in place to protect your organization and its assets from Advanced Persistent Threats.
Evaluate your public operations
Security leaders must consider the nature of the organization's operations, foreign office and facility locations, public profiles and positive and negative press that might make them an attractive target for Advanced Persistent Threat actors.
In addition, certain international locations can raise your organization's visibility to nefarious elements that may wish to gain access through employment. This threat vector, an actor operating in the guise of an employee, represents a very challenging problem for information security personnel. As a result, it is imperative that security personnel understand any country- or location-specific circumstances that dictate specialized physical and logical security controls.
Security personnel should be sensitive to what information about operations that is easily accessed on the Internet. Leaked or stolen credential data can give adversaries exactly what they need to gain access to your networks, systems and data. In addition, information security personnel should establish a process to periodically review what files exist publicly online that your own organization has published. Include review of the metadata associated with each file and this may yield information useful to an adversary.
Identify your assets
Your organization likely has a mix of assets of interest to an adversary. Working closely with the business, security professionals should catalog the organization's assets and rank their importance to the overall financial performance of the organization. Assets include Intellectual Property, confidential information, sensitive customer and employee records, financial and strategic information, product information, etc. Information security professionals should try to evaluate the organization's assets through the lens of the adversary.
Value is the ultimate measure for any determination of risk to attack from Advanced Persistent Threat (APT) actors. Though assets and information can be assessed on many different attributes, placing a monetary value is critical. We've provided perspectives here for organizations to consider:
Substantial positive valuation
Most organizations are likely to consider the positive business impact or market value of their assets. This is a good measure for the value of assets that produce some type of financial return but may not be a good measure for placing value on assets such as customer or employee records which Advanced Persistent Threats are after.
Substantial negative valuation
The estimated cost from a breach is useful for identifying assets that do not generate any direct positive financial value but for which a value is needed to assess their overall importance of the organization. For instance, though customer records may not yield any direct positive financial gain, their disclosure to the public by an APT will likely incur significant cost to the organization.
Company/brand perception and cost
Organizations must carefully evaluate the implications of a major information security breach by an Advanced Persistent Threat on the company's brand image in the marketplace. A decline in brand value can contribute to lost sales immediately after the event and compound in the future. In addition, in the case of publicly-traded companies, a negative market perception can reduce the trading value of the stock which in turn erodes the organization's market capitalization.
Assess the vigilance of your employees
APT actors will use the simplest, most effective tools at their disposal first to obtain information and penetrate your networks. This includes social engineering and phishing which target your executives and employees to give up valuable information or access through seemingly innocent pretexts.
Organizations should regularly test your employees' security awareness and promote processes to report suspicious activity to the Office of the Chief Information Security Officer or other security leadership.
Consider your affiliate relationships
Advanced Persistent Threats actors may use your organization as a pass-through to partners and affiliate relationships, or look to gain access to your networks and systems through those partners and affiliates.
Information security personnel must consider security both in terms of logical and physical access that an affiliate may have. Also, security personnel should consider the affiliate's internal security processes and how they might raise risk to the primary organization.
Phase Two: Identify Risk from Advanced Threats
Correlate your current state to the risk from Advanced Persistent Threat (APT) actors.
This phase takes the information collected in phase one and maps that information to what we know about Advanced Persistent Threats to determine the risk of exploit to your organization.
The potential market value of your identified assets contributes to your organization's attractiveness to APT adversaries. However, keep in mind that your organization may also be targeted regardless of the assets it has.
Use the graphic below to further evaluate your risk from Advanced Persistent Threat actors (delineated by the upper blue portion of the diagram).
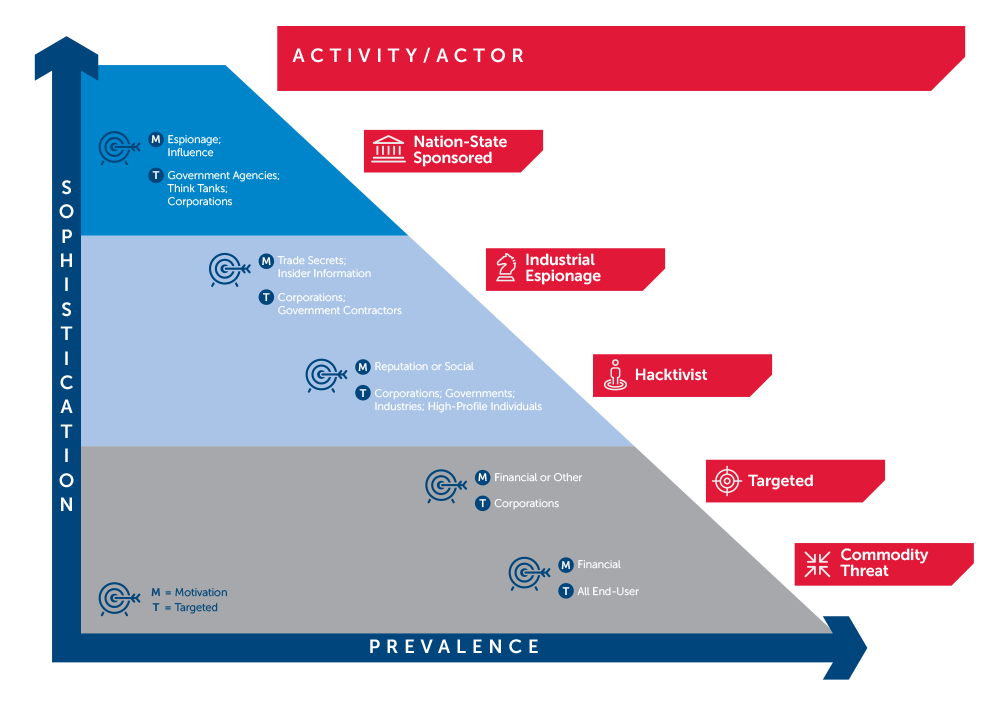
Your risk from Advanced Persistent Threats
When your risk is mostly from "commodity" threats
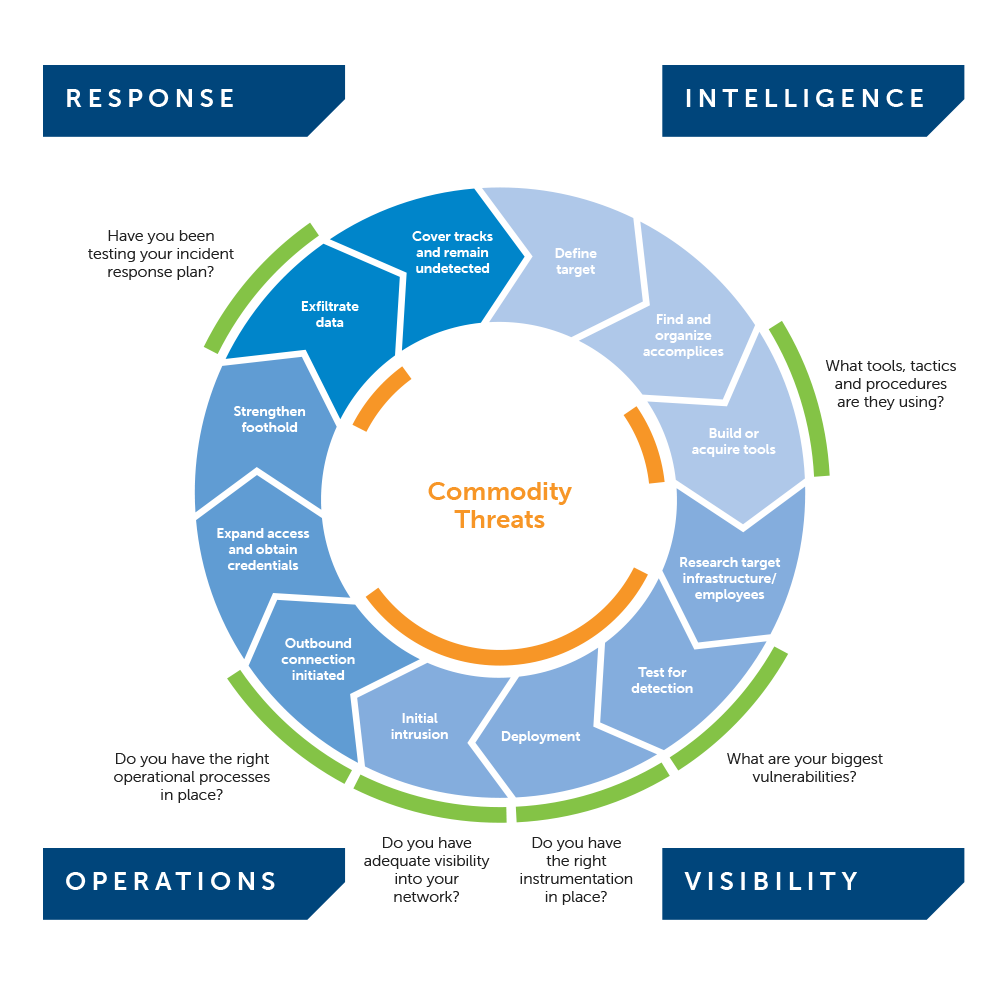
For organizations largely at risk of "commodity" or broad-based threats, having visibility into your networks and systems to identify commodity threats is critical. In addition, a robust Incident Response capability is critical to effectively respond to a security breach and reduce its duration and overall cost. Though forward intelligence on targeted threats to your organization isn't prudent, threat intelligence on emerging threats in a global context is useful (watch a three minute video on global threat intelligence).
When your risk from hacktivists is significant
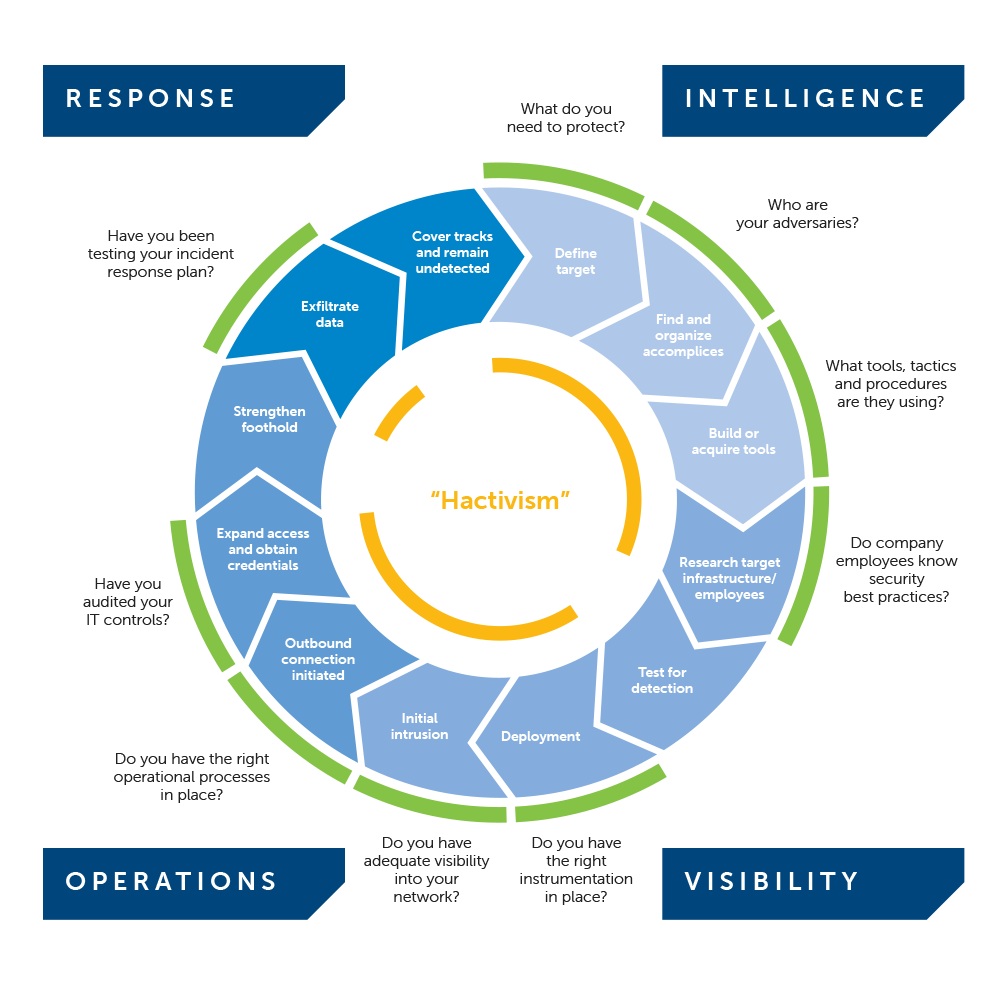
At any time, your organization, brand or executives could be at risk of attacks by hacktivists. Though hacktivism is not considered an Advanced Persistent Threat because threats typically lack the same level of sophistication, organization and resources, hacktivism can still represent a significant threat to organizations. If hacktivism is a concern, security personnel should work to establish mechanisms to monitor for hacktivist activity and attack planning against their organizations. This is mostly accomplished by intelligence activities centered on targeted threats to your specific organization and designed to identify and assess security threats before they can have an impact.
When you've deemed your risk from an Advanced Persistent Threat is significant
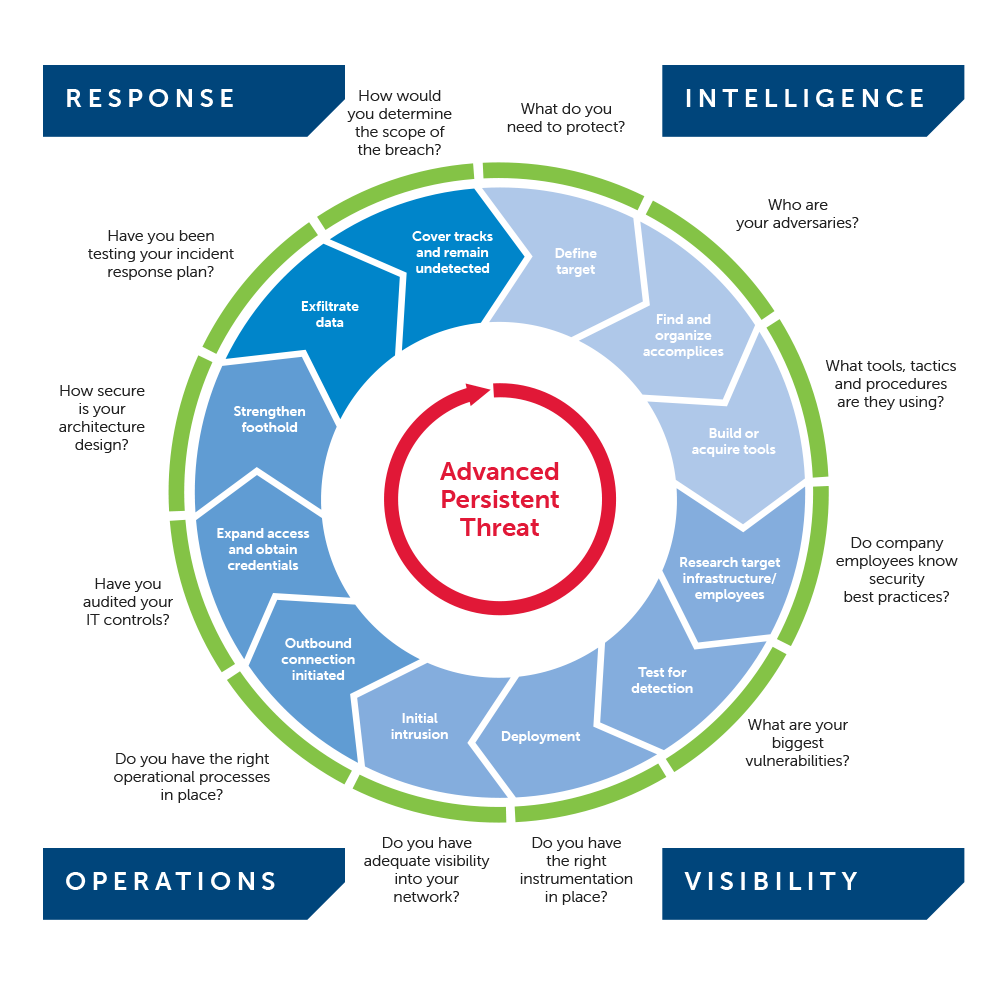
For those organizations at higher risk of attack by Advanced Persistent actors, continue to Phase 3.
Phase Three: Articulate and Implement your Vision
How do you articulate your vision and what critical components do you consider?
For those organizations where there is a greater risk of exploit by an Advanced Persistent Threat (APT) actor, security leadership will need to design and implement a revised security vision or strategy to address the threat.
Effectively defending against Advanced Persistent Threats will force many organizations to revisit their current security strategies to address the numerous areas adversaries can exploit.
The graphic below depicts the core capabilities identified by SecureWorks as required when devising a strategy against Advanced Persistent Threats: Intelligence, Visibility, Operations and Response.
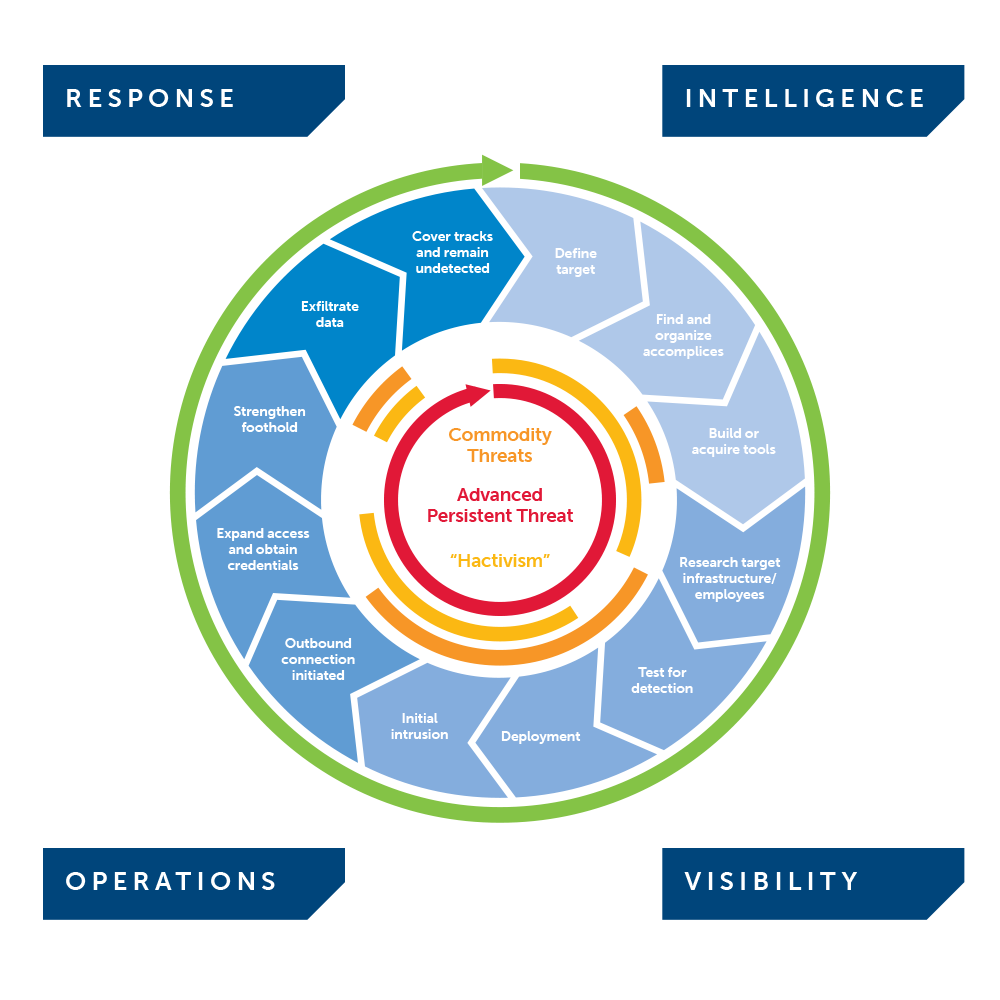
Intelligence
Organizations should look to deploy forward intelligence capabilities that provide actionable information on Advanced Threat actors including APT and their operations. Regardless of the generalized or specific nature of the intelligence, it must be actionable to allow security leaders and personnel to make decisions and take action to enhance the organization's security posture.
Visibility
Security teams must have full visibility into the operations and security of their systems, networks and assets. Organizations must evaluate their current security architecture and consider recalibrating security policies to ensure that the right information is being correlated to give security professionals a view of the "big picture." This big picture view may be instrumentation in a "dashboard" representation. Having visibility into what is happening behind the firewall is just as important as what is trying to penetrate the firewall from the outside.
Operations
Security leaders must evaluate the capabilities of their current operations and personnel. Leaders must answer whether their operations are efficient and effective and if not, how they can be improved. This includes assessing the in-house expertise and constraints on that expertise to monitor and address advanced threats in real time. This may be accomplished in assessing overall security strategy.
Response
Because there is no "silver bullet" to protect against Advanced Threats one hundred percent of the time, organizations must evaluate their capability to respond effectively to an incident.
Security leaders and personnel should take an introspective look at their organization to determine if the organization is adequately prepared to respond effectively to a breach by an Advanced Persistent Threat actor. As such, it is critical your organization has a Computer Incident Response Plan (CIRP) in place detailing and that the plan is robust and tested.
Defense-in-Depth with Forward Operating Intelligence and Incident Response Capabilities
Advanced Persistent Threats heighten the need for a broad, layered security or "defense-in-depth" model.
The illustration below highlights how the defense-in-depth model must evolve to address Advanced Persistent Threats and changing technologies, such as mobility and cloud computing that expand the network edge, and the attack surface adversaries could exploit. This model addresses the four capabilities of Intelligence, Visibility, Operations and Response.
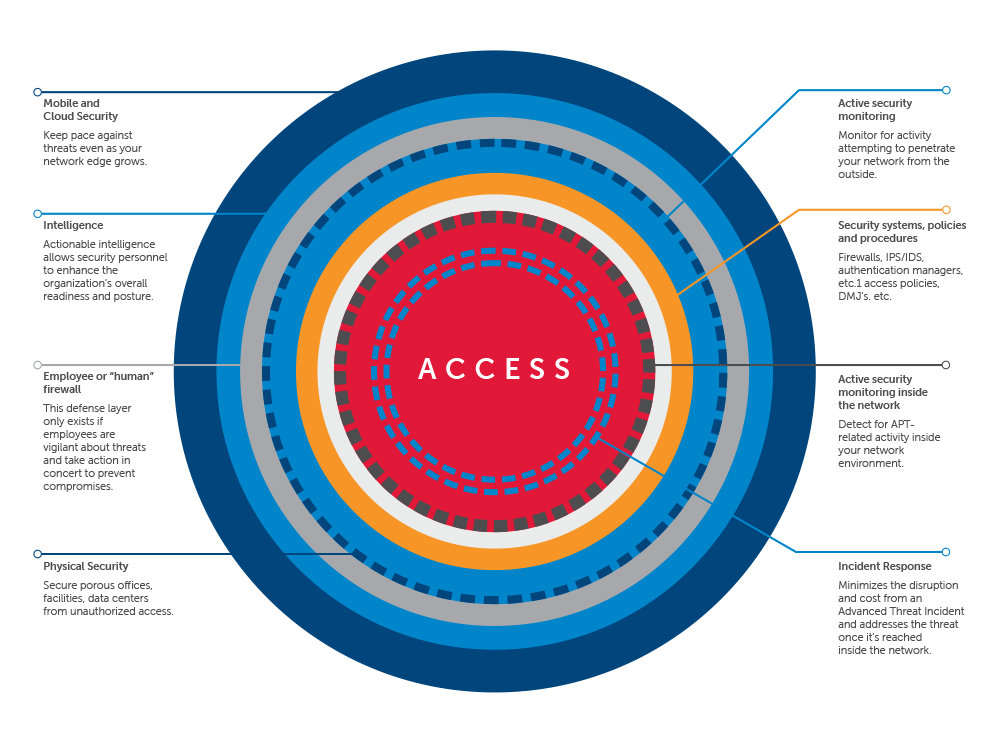
Address these key areas:
Protect your organization and its assets
Protecting your organization against Advanced Persistent Threats involves addressing all four areas of the Advanced Threat lifecycle - Intelligence, Visibility, Operations and Response - that makes the most sense for your organization. Security staffs can and should develop a stronger security posture that is both resilient and prepared for all threat scenarios, including when a threat reaches into the network.
Know in advance when organized elements may be targeting your organization
Organizations can develop a forward operating capability through targeted threat intelligence as part of their overall security strategy. This includes tapping into the “conversations” that may be taking place across the Internet by persons or groups who may be targeting them, assessing the risk from information their own employees are making available in the public sphere, and obtaining general and specific threat intelligence to alert the organization to potential threats. Organizations then have an opportunity to preempt planned attacks by preparing their employees and security defenses based on the information they have obtained through their forward operating capability.
Detect advanced attacks when they are at your doorstep
Organizations can develop more robust security architectures, policies and monitoring that help to identify Advanced Persistent Threats when they strike and prevent their penetration. In addition, security staff can develop their knowledge and expertise to understand what signs to look for to identify and respond to an Advanced Persistent Threat. However, given the sophistical and approach many actors may take, detection is just one element of any effective security strategy against Advanced Persistent Threats.
Determine if your organization has already been compromised
Forensic analysis including log collection, monitoring and review can be used to detect an existing threat. Security staff that is concerned that a major breach may have already occurred can and should contact a third party digital forensics provider to perform a formalized investigation, including collection of evidence. However, finding an existing threat can be like finding a needle in a haystack. So, policies should be designed to detect changes in access rights, access to systems, data and information that is out of the norm and detect and prevent exfiltration of sensitive information.
Improve the vigilance of your employees
Social engineering and phishing represent very common and very effective methods that Advanced Threats can glean useful information to further their objectives when attacking your organization. However, organizations can raise the vigilance of their employees through periodic testing. Regularly training and testing your employees to become more vigilant and effective against social engineering or phishing must be a cornerstone of your security strategy to combat Advanced Threats.
Phase Four: Test & Enhance Your Security
How do you ensure that your security strategy adapts to a changing threat landscape and remains effective?
Given the sophistication, organization and persistence of Advanced Persistent Threats (APT), testing of security capabilities and policies is critical to promote continuous improvement.
Testing on multiple levels
Testing should address security from logical (systems, networks, applications, etc.), physical (offices and facilities) and employee (susceptibility to social engineering or phishing activities) standpoints.
Testing cannot be considered optional against Advanced Persistent Threats
For organizations especially concerned about their risk from Advanced Persistent Threats, a multi-faceted testing regimen is prudent. Testing options include technical testing such as penetration testing and full-scale red team simulations, social engineering and phishing to test employees, and tabletop and wargaming exercises to test and improve Incident Response preparedness.
Secureworks has been acquired by Sophos. To view all new blogs, including those on threat intelligence from the Counter Threat Unit, visit: https://news.sophos.com/en-us/.

