Summary
SecureWorks' research team has detected a Mocbot variant in the wild utilizing the MS06-040 vulnerability in order to spread in a worm-like fashion.
File Details
Filename: wgareg.exe
Filesize: 9,609 bytes
MD5: 9928a1e6601cf00d0b7826d13fb556f0
SHA1: 352a276346eabde7bfce9efee732a973e0d26baa
Packer: MEW
CME Number: none assigned
Analysis
Mocbot first appeared in late 2005, using the MS05-039 PNP vulnerability in order to spread. Since it is fairly unremarkable IRC bot and was not even the first to use the MS05-039 exploit, it received little attention past the ordinary anti-virus writeups and signatures.
Amazingly, this new variant of Mocbot, still uses the same IRC server hostnames as a command-and-control mechanism after all these months. This may be partially due to the low-profile it has held, but also may be due to the fact that the hostnames and ip addresses associated with the command-and-control servers are almost all located in China. Historically Chinese ISPs and government entities have been less-than-cooperative in taking action against malware hosted and controlled from within their networks.
Little appears to have changed between previous Mocbot variants and the new one, except the replacement of the MS05-039 exploit with that of MS06-040. Primarily Mocbot resembles many other IRC bots, providing the controller with a backdoor on the infected host, along with the ability to launch a DDoS attack against other hosts, as well as being able to use the built-in exploit to spread to additional systems.
This variant of mocbot copies itself to the system directory as wgareg.exe, and creates an NT service to run at startup called "Windows Genuine Advantage Registration Service". The description given to the service reads "Ensures that your copy of Microsoft Windows is genuine and registered. Stopping or disabling this service will result in system instability.", in an attempt to discourage users from stopping it from running.
Mocbot can also use AOL Instant Messenger to send instant messages using the victim's account. This could be a potential vector to allow the controller to trick users into downloading and executing the bot from an external URL, allowing it to penetrate firewalls like any other file downloaded over HTTP. Once inside a network, it could then spread using the MS06-040 exploit to vulnerable internal systems over TCP port 445. This underscores the danger of allowing unrestricted external instant messaging in a corporate environment, as it often introduces malware directly to users, bypassing perimeter controls.
At the time of this writing, anti-virus detection is not especially broad, with only 1/3 of all anti-virus engines tested reporting the file as malware or flagging it as suspicious. None of them recognize it as a Mocbot variant.
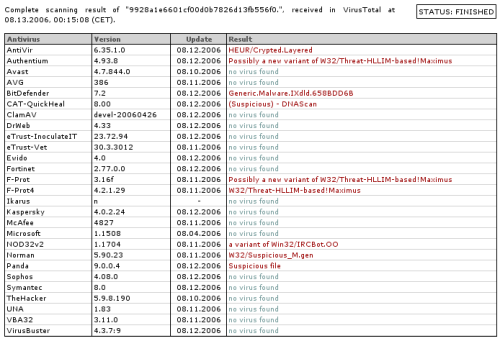
Image courtesy of VirusTotal
The hard-coded command and control servers are:
- bniu.househot.com
- ypgw.wallloan.com
The IP addresses currently pointed to by these hostnames are:
- 58.81.137.157
- 61.163.231.115
- 61.189.243.240
- 202.121.199.200
- 211.154.135.30
- 218.61.146.86
Update
A second variant has been detected - it uses the same command-and-control servers, and is named wgavm.exe, with a service name of "Windows Genuine Advantage Validation Monitor". The md5sum of the second variant is 2bf2a4f0bdac42f4d6f8a062a7206797, and its sha1sum is 339717f8b50580ab1af41c15436e10651382952. The file size is only 9,374 bytes, suggesting it may in fact be a precursor to the variant described above. However, as the MEW packer destroys the compiler timestamp in the PE file, there is no way to be 100% certain.
Solution
Even though the vulnerability exists in all service pack levels of Windows XP/2003/2000/NT, the exploit is not known to work on XP SP2 or Windows 2003 SP1 - XP/2003/2000/NT versions below these latest service packs are most at risk. Install the Microsoft-provided patch in order according to the risk posed to each system. Note that even a failed exploit attempt could still result in a system crash, so all Windows workstation and server systems need to be patched.
Because of the reduced numbers of outdated systems brought about by patching due to previous worms/spyware, plus other factors, it is expected that Mocbot and any other bots/worms utilizing the MS06-040 exploit will be less successful than similar previous worms. The most recent example is Zotob, which was largely unimpacting to the Internet as a whole, even a year ago.
Snort Signatures
The following Snort signatures written by the SecureWorks research team will detect the exploit used by Mocbot and other known PoC MS06-040 exploits. They have been released to the Bleeding Snort project.
alert tcp any any -> any 139 (msg:"NETBIOS SMB DCERPC NetrpPathCanonicalize request (possible MS06-040)"; flow:to_server,established; content:"|00|"; depth:1; content:"|FF|SMB|25|"; depth:5; offset:4; nocase; byte_test:2,^,1,5,relative; content:"&|00|"; within:2; distance:56; content:"|5C|PIPE|5C 00 05 00|"; within:9; distance:4; content:"|1f 00|"; distance:20; within:2; reference:url,www.microsoft.com/technet/security/bulletin/MS06-040.mspx; classtype:misc-attack; sid:2003081; rev:1;)
alert tcp any any -> any 445 (msg:"NETBIOS SMB-DS DCERPC NetrpPathCanonicalize request (possible MS06-040)"; flow:to_server,established; content:"|00|"; depth:1; content:"|FF|SMB|25|"; depth:5; offset:4; nocase; byte_test:2,^,1,5,relative; content:"&|00|"; within:2; distance:56; content:"|5C|PIPE|5C 00 05 0|"; within:9; distance:4; content:"|1f 00|"; distance:20; within:2; reference:url,www.microsoft.com/technet/security/bulletin/MS06-040.mspx; classtype:misc-attack; sid:2003082; rev:1)
Update: Aug 15, 2006
We've followed up our analysis of Mocbot with an analysis of the spam trojan installed by Mocbot and the motivation behind the entire episode.
Secureworks has been acquired by Sophos. To view all new blogs, including those on threat intelligence from the Counter Threat Unit, visit: https://news.sophos.com/en-us/.
