In September 2023, Secureworks® incident responders investigated a network compromise that originated from a phishing email containing a PDF attachment. The PDF included a QR code that directed recipients to malicious content hosted on an interplanetary file system (IPFS) gateway (see Figure 1). Using this gateway allows threat actors to save the cost and effort associated with hosting their own infrastructure and makes it difficult for law enforcement to take down the malicious content.

Figure 1. PDF email attachment containing a QR code directing users to a malicious phishing site. (Source: Secureworks)
The URL extracted from the QR code (https: //dynamicgpr . com/cs/index (1).php/?cfg=<46-character string>==) contains a cfg parameter that appears to be unique to each targeted organization. Scanning the QR code with a mobile device directs victims to this URL, which steals session tokens and redirects to an ipfs . io gateway that hosts a malicious sign-in page to harvest Microsoft account credentials (see Figure 2).
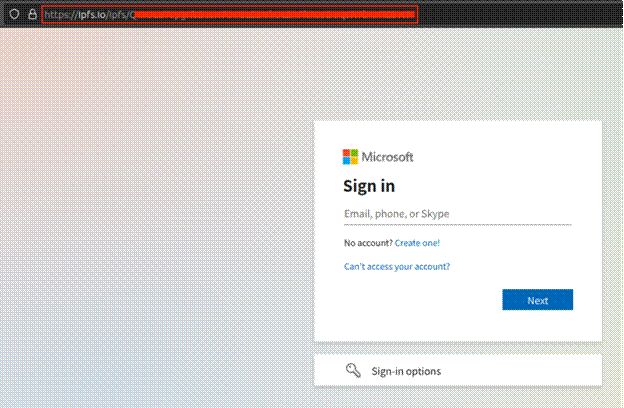
Figure 2. Malicious Microsoft sign-in page hosted on an IPFS gateway. (Source: Secureworks)
The first successful sign-in activity to the email account originated from the malicious Bulgarian IP address 91 . 92 . 109 . 80. Approximately two minutes after this initial login, the threat actor installed an authenticator application for multi-factor authentication (MFA) and created an inbox rule to delete incoming emails from the victim's domain. Later the same evening, this compromised email account accepted an application consent grant from Microsoft IP address 20 . 55 . 51 .76 giving the requester access to an application named 'PerfectData Software'. This legitimate tool exports mailboxes for backup purposes.
PerfectData Software was reportedly used in another malicious Microsoft 365 account takeover that involved the tactics, techniques, procedures (TTPs) observed by Secureworks incident responders. In both incidents, the threat actors signed into a compromised Microsoft 365 account from an endpoint associated with a virtual private network (VPN) or virtual private server (VPS) service, registered the PerfectData Software application, accessed mailbox data, and then created inbox rules. The Secureworks IR investigation did not reveal other accounts with the application consent grant, and the application was removed four days after the initial compromise.
Secureworks incident responders identified that the compromised account had received a phishing email with an attachment named 'Francophoneprojects Stub#45888 .pdf'. Secureworks Counter Threat Unit™ (CTU) analysis of the sender email address revealed a similar message posted to the VirusTotal analysis service. The VirusTotal sample was sent from the same email address to a multinational construction and real estate company and also contained an attachment with the string 'Paystubs#503' in its filename. The attachment sent to the construction company claims to be a payroll update request and includes the victim's logo and company name in the privacy disclaimer to appear legitimate. The QR code in that attachment redirects to the same domain as the sample analyzed by Secureworks incident responders.
CTU™ analysis of this domain revealed 65 additional files uploaded to VirusTotal between September 13 and September 20. Most of these files are PDFs, and many of the filenames follow a similar naming pattern to the sample in the Secureworks IR engagement. These PDF files also contain the same layout and boilerplate language, except for the victim-specific elements. The victimology does not suggest that a specific sector was targeted, as victims represent a range of geographies and industries.
While many of the samples used the payroll theme, some of the PDFs indicated that the QR code was part of an MFA security upgrade. It is unclear if the differences were due to varying objectives or to factors such as the victim's sector or location. In all of the identified samples, the QR codes led to a malicious document hosted on an IPFS gateway.
CTU researchers have observed an increasing number of phishing attacks using QR codes (also known as Qshing) to bypass conventional email filters that rely on static or dynamic analysis of message content. Unlike many conventional phishing attacks, QR codes require the victim to scan the image with a mobile device. This requirement broadens the attack surface and increases the likelihood of success, as it forces the victim to use an additional device that may not be as secure as a corporate system. Additionally, corporate security controls may not have visibility of communication that occurs via a personal device.
CTU researchers recommend that organizations educate employees about the dangers of QR phishing and the importance of exercising caution before scanning any QR code. Organizations should implement a process for reporting suspicious emails and for validating that a QR code was sent from a genuine source for a legitimate business purpose.
To mitigate exposure to this malware, CTU researchers recommend that organizations use available controls to review and restrict access using the indicator listed in Table 1. The domain may contain malicious content, so consider the risks before opening it in a browser.
| Indicator | Type | Context |
|---|---|---|
| www.dynamicgpr.com | Domain name | Phishing website embedded in QR code |
| 91.92.109.80 | IP address | Origin of unauthorized email login in QR code phishing attack |
Table 1. Indicators for this threat.
Phishing is a common attack vector. Read about another phishing campaign targeting Booking.com customers and properties. If you need urgent assistance with an incident, contact the Secureworks Incident Response team.
Secureworks has been acquired by Sophos. To view all new blogs, including those on threat intelligence from the Counter Threat Unit, visit: https://news.sophos.com/en-us/.
