Dell SecureWorks Counter Threat Unit™ (CTU™) researchers analyzed a stealthy malware family named Stegoloader that has been active since at least 2013 and yet is relatively unknown.
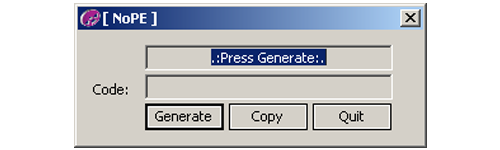
It has been distributed through software piracy websites, bundled with software license key generators (see Figure 1).
Figure 1. Key generator that installs Stegoloader. (Source: Dell SecureWorks)
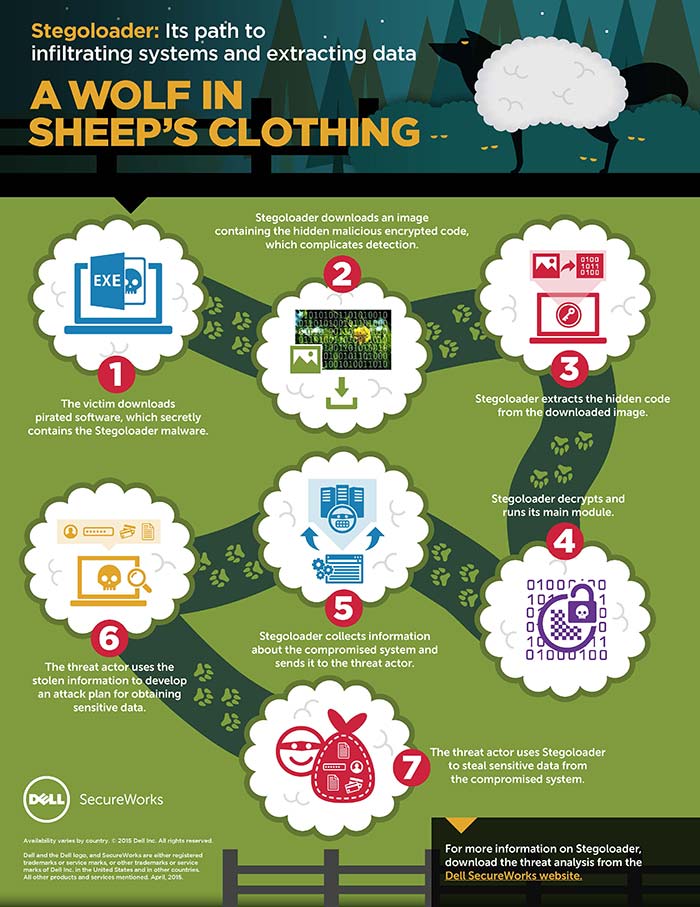
Stegoloader’s core component is hidden in a Portable Network Graphic (PNG) image hosted on a legitimate website. The malware downloads this image each time it runs and uses steganography to extract its code from the image. The malware is never saved to the hard disk and is executed directly from memory, which makes detection difficult.
Furthermore, some of Stegoloader’s features are deployed only on compromised systems of interest to the malware operator. Various modules provide additional functionality:
- Geographic localization module — Obtains the compromised system’s public IP address.
- History module — Sends a list of recently opened documents to the malware operators.
- Password stealing module — Collects and sends credentials for most popular applications.
- IDA stealing module — Locates and steals data associated with the IDA reverse engineering tool. This module, which is deployed only to compromised systems that have IDA installed, steals installation files and registration keys, and uploads them to a file-hosting website.
Stegoloader continues a trend of malware using steganography to evade host-based and network-based detection. This behavior was previously observed in the Lurk and Neverquest malware families. Stegoloader also incorporates the trend of opportunistically deploying functionality. Modules to extract specific information are used as needed, making forensic analysis challenging.
Figure 2 shows Stegoloader’s process. CTU researchers have also published a full analysis of the malware on the Dell SecureWorks website.
Figure 2. Stegoloader process. (Source: Dell SecureWorks)
Secureworks has been acquired by Sophos. To view all new blogs, including those on threat intelligence from the Counter Threat Unit, visit: https://news.sophos.com/en-us/.


