Media Alert: Top Ransomware Families Making Their Way Through APAC Region
ATLANTA, Aug 25, 2016-–SecureWorks® Counter Threat Unit™ (CTU) researchers have tracked the spread of several notorious ransomware families to the Asia-Pacific region, underscoring efforts by some attackers to localize their tools to target multiple geographies.
According to the CTU™ research team, the current top four ransomware families - Locky, Cerber, CryptXXX and TorrentLocker – are targeting computer users in Japan with localized versions of their threats. In addition, the threat actors behind CryptXXX have developed a localized version for South Korea as well.
“Unlike other types of malware that are mostly designed to compromise the system covertly, ransomware requires end-user interaction to achieve its goal – collecting ransom,” explained SecureWorks researcher You Nakatsuru. “This makes localizing the threat particularly useful to attackers.”
Localization can take one or all of the following forms: attackers can write ransomware messages in the local language; strategically compromise local websites; deliver the ransomware via spam campaigns in the local language; or provide payment instruments using local bitcoin wallet and exchange market lists.
In Japan in particular, SecureWorks has noted a spike in ransomware infections starting in 2015. Before that, ransomware infections were not that common in the region because ransomware was primarily delivered via spam emails written in English. As a result, Japan-based computer users tended not to fall prey to the malicious emails. However, since 2015 there has been an uptick in ransomware in the area being distributed using exploit kits, and ransomware authors have started developing multi-language ransomware such as Locky.
The effort by cyber attackers to localize their weapons highlights the importance of information sharing and situational awareness, as a threat in one geographical region can soon become a threat in another. Below is a chart of when several ransomware families were initially spotted in the region by members of the security community. The dates noted in the table below are the first reported dates from each Asia-Pacific country’s national Computer Security Incident Response Team.
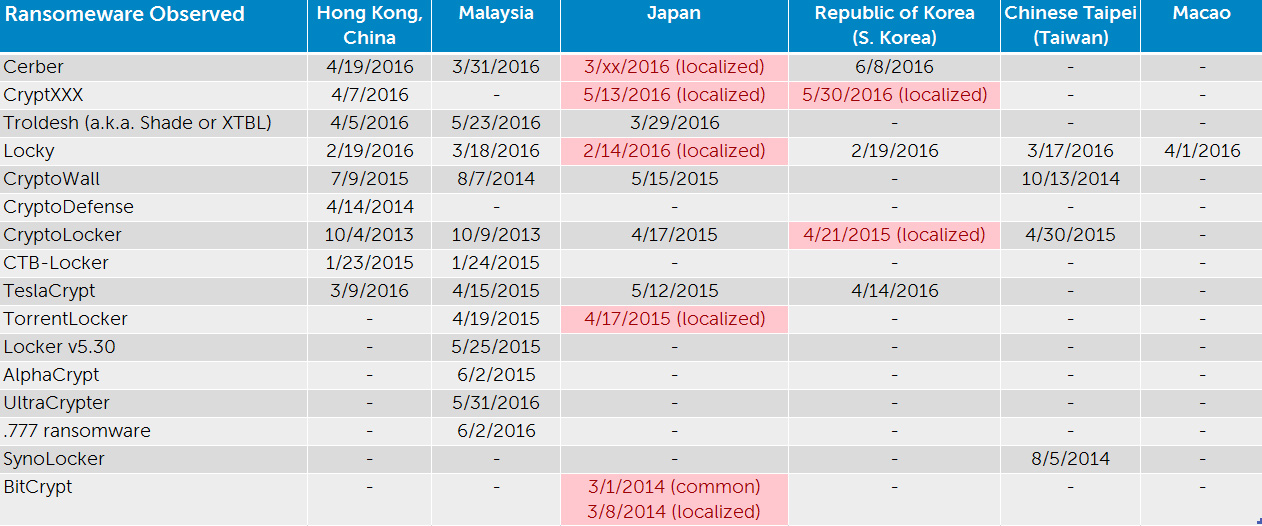
Table 1. Initial ransomware incident reported in each geographical area
CTU™ researchers discovered that the Locky ransomware was being used by threat actors to target computer users in Asia-Pacific during Q12016, the very same time the ransomware was being used to infect victims in North America and EMEA, indicating that the threat actors were targeting multiple countries during the same timeframe.
Localization can happen at different paces. For example, despite the English version of CryptXXX being reported in the region in April 2016, a localized version of the ransomware was not reported in Japan and South Korea until May 2016.
In contrast, the CTU™ team noted that it took nearly a year and a half for a localized version of CryptoLocker to be identified in South Korea after the English version was reported in Hong Kong. This localized version is believed with moderate confidence to be the work of a different group. However, in the case of CryptXXX, the CTU™ research team believes with moderate confidence that the localized variant that appeared in May is the work of the same threat actors using CryptXXX elsewhere in the region.
Any time gap between the discovery of threats in different regions offers an opportunity for other areas to proactively protect themselves against attacks. While “local” malware variants may use different infrastructures and network indicators, such as IPs and domains, countermeasures designed to detect/filter ransomware command and control (C2) packets will be still effective unless significant change in C2 protocol occurs.
