- Author: Joe Stewart, Director of Malware Research, SecureWorks
- Date: October 15, 2008
Introduction
Earlier this year, notorious spammer Alan Ralsky was indicted in a federal case alleging his involvement in illegal spamming and stock fraud. In a 41-count indictment, Ralsky was charged with using a botnet to send "pump-and-dump" spam for various Chinese penny stocks. At nearly the same time, the botnet created by the malware known as Warezov (also Stration or Opnis), long known for spewing stock spam, also fell silent.
It is unclear whether Warezov was used by Ralsky or whether the botnet operators behind Warezov were just spooked by the arrest and decided to lay low for a while. But, as of 2008, it appears Warezov is back in the spamming business - but operating differently this time.
Propagation
Warezov was historically spread via email attachments, however that activity has also largely ceased. These days, executable attachments via email are almost universally blocked. Most botnet operators have switched to installing via browser/plugin exploits or social engineering. Warezov is no different. Only a few days ago, we saw Warezov being spread through a site advertising free MP3s via download of a P2P program:
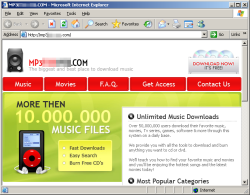
No exploits were used here, just social engineering. The user has to choose to install the software, which is simply the Warezov trojan.
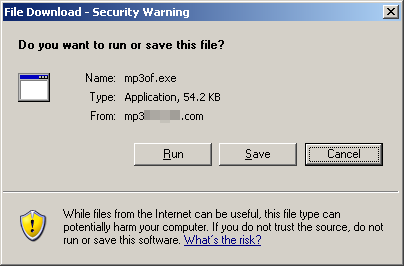
There's not even a fake installer or any dialogue presented to the user at all after this point, the software simply runs in the background, leaving the user to think their brand-new P2P client installer simply crashed or failed to work.
Fast-Flux
Like many botnets, Warezov is really a payload delivery system. It can install any software the botnet operator wishes. Since the end of the stock spamming activity, Warezov has mainly served as a "fast-flux" hosting platform, allowing spammers to hide the true origin of their spam websites behind an infected node's IP address. The IPs for a spam domain can be rotated so fast it is impossible to have the hosting taken down. Warezov accomplishes this activity by installing two components: a reverse HTTP proxy that serves the content from a hidden master server, and a DNS server which is actually a customized installation of the popular ISC BIND software compiled for Windows. Each DNS server acts as a slave which gets zone updates from the hidden master server.
The actual named.conf file from the Warezov installer is shown below:
options {
recursion no;
additional-from-auth yes;
additional-from-cache no;
max-cache-ttl 60;
max-ncache-ttl 60;
allow-query {any;};
lame-ttl 0;
dnssec-enable no;
min-refresh-time 59;
max-refresh-time 61;
};
zone "thisistestdomain.ntd" IN {type slave; masters {208.72.169.21;};};
zone "." IN {type slave; masters {208.72.169.21;};};
From Atrivo to McColo
In the past, Warezov has often had its C&C servers hosted by Atrivo/Intercage. However with the recent shutdown of that service, Warezov has switched to another hosting service well-known to malware incident responders: McColo Corporation. Like Atrivo/Intercage, this provider has something of a reputation for frequently hosting botnet control servers. It's not the only one, but it is one of the most popular in the Russian spam underground. Currently McColo hosts C&C servers for some of the biggest botnets - Rustock, Srizbi, Pushdo/Cutwail, Ozdok/Mega-D and Gheg all have part or all of their master control servers hosted by McColo. When Atrivo was de-peered, the world saw a brief drop in the output of spam. If McColo were ever to suffer the same fate, worldwide spam output would probably be cut in half (until each botnet operator found new hosting, which wouldn't be long).
Like Atrivo, McColo also has a few legitimate customers for plausible deniability. Like Atrivo, they will also respond to abuse complaints. However, in our experience, this simply means the botnet C&C will be moved to a new IP address within the McColo network. But, rather than call for the removal of AS26780 (McColo's Autonomous System number) from the Internet as some others might, we rather like knowing where the bulk of the bad activity is coming from, so protecting our networks is easier. Even if every "bad" colocation/hosting service is removed from the net, criminals will simply host everything on fast-flux networks made up of compromised desktop machines, and everything will be more spread out and harder to mitigate.
Hotmail Spam
Most of the time botnets aren't really given any special attention unless they are prolific emitters, either of DDoS or spam. Fast-flux is seen as a problem, but not as pressing of an issue as packets hitting ones network or mailservers. So Warezov could have faded into the background noise of the Internet and continued to operate indefinitely. However, on or around October 7, 2008, Warezov began emitting spam again. Only this time, it was not sending direct-to-MX spam as before - it is now deploying a tool to send spam via Microsoft's Hotmail service. A bot we were monitoring downloaded the following file:
http://localhost-2.com/wmml1.[blocked].exe
Not long after, we saw the following requests sent by the bot:
http://masedinkionderunhasdeun.com/[blocked]/msn_imailer_v7.txt
http://s1.masedinkionderunhasdeun.com/[blocked]/tasks/task_264_letter_1223431382.txt
masedinkionderunhasdeun.com fits a well-known pattern seen in previous Warezov domain names, which is long, nonsensical-yet-phonetically-pronounceable names. Here are just a few of many previously seen Warezov domain names:
asedrunkionyunhasde.com
cadesfinjeriokas.com
fandesjinkderunha.com
hertionkadesinpoion.com
kykbonsa.com
madesunjinkdieonrunhasde.com
pazmogutionsa.com
rasetikuinyunhderunsa.com
sadefunkionyunhderuns.com
vedasetionkderun.com
yuhadefunjinsa.com
However, other more meaningful domain names are also part of the Warezov operation:
localhost-2.com
grand-sale-4.com
discount-pharmacy-online-e.com
checkthisservice.com
Inside the task file downloaded from s1.masedinkionderunhasdeun.com was the following content:
<html>
Good afternoon!<br _moz_dirty=""/>
<br _moz_dirty=""/> <br _moz_dirty=""/>
<br _moz_dirty=""/> <br _moz_dirty=""/>
<font size="6" _moz_dirty=""> Cialis Soft Tab as low as $3.22 <a _moz_dirty="" href="http://www.take-this-please-4.cn/">http://www.take-this-please-4.cn/</a></font><br _moz_dirty=""/>
<br _moz_dirty=""/> <br _moz_dirty=""/>
Best regards,<br _moz_dirty=""/>
Matt Hough<br _moz_dirty=""/>
<br _moz_dirty=""/> <br _moz_dirty=""/>
</html>
The bot was also given a list of Hotmail usernames and passwords which appeared to be automatically generated. Each username is used to send only a few emails with an average of five recipients each, in order to defeat any rate-limiting that Hotmail may be using to thwart this type of activity. It is unclear what method is being used to defeat the Hotmail account-creation CAPTCHA system, but it is commonly known that the system has been defeated by spammers, either by optical character recognition or human "account farming" operations.
Reputation Hijacking
What the spammer is engaged in here is known as "reputation hijacking". Mail sent direct-to-MX by spambots is increasingly being blocked by various blacklists such as the Spamhaus XBL and PBL. Residential and small-business broadband IP addresses that send spam are given a bad reputation by these services, which are checked by various anti-spam systems. In order to increase deliverability rates, spammers are abusing webmail systems such as Hotmail, Yahoo, AOL and others, knowing that mail from these systems can not be blocked wholesale by receivers without blocking legitimate mail as well. So the spammers hijack the good reputation of big mail services in order to get their spam through the filters.
We are seeing a trend towards webmail reputation hijacking by other malware such as Wopla or Hotlan. However, this trend may be short-lived, as there are many obstacles for the spammers to overcome which diminish the efficiency and overall profitability of sending spam this way. Unlike SMTP, which is a universal and stable protocol, creating webmail accounts and sending spam through them requires that the spammer constantly change the botnet code to adapt to protection methods employed by the webmail service. This may sound like the typical "cat-and-mouse" game that spammers have been playing with anti-spammers for a while in regards to spam filtering. But there is a slight difference - Previously spammers only had to adapt their spam content to defeat filters - now they have to be able to programatically respond to changes in the webmail system, which requires them to pay for highly skilled programmers and possibly other services (OCR/account farmers) in order to maintain their spamming capacity.
There is a slight advantage to the defenders here - it is far easier for a single webmail provider to deploy a spambot countermeasure than to update the SMTP protocol. New anti-fraud measures like Pramana's HumanPresent system that go beyond simple CAPTCHA may also prove daunting to spammers in the future as they attempt to abuse web-based registration systems. At the same time, while SMTP was designed for efficient delivery to a large number of recipients, webmail systems can be limited to low-volume email without disturbing the average user. For all these reasons, reputation-hijacking may never be the overwhelming force in spam that direct-to-MX botnets have been.
Conclusion
Regardless of what methods are in use, spam is not going away any time soon. There is clearly too much money involved in spam and as a result, botnets. Because of this, we doubt Warezov will cease operations in the near future. Despite indictments that may exist in the U.S., there are too many obstacles, both technical and political, that make it nearly impossible to get Russian botmasters arrested. And the botmasters are quite aware of this fact, allowing them to operate brazenly and without fear. Warezov is no different in this than a dozen other major spam operations. Until spam and botnets become a problem for Russian citizens, we expect no change on this front.