- Author: Joe Stewart
- Date: 13 November 2006
In an earlier analysis, we revealed a botnet created by a trojan sometimes called SpamThru. By working with the anti-spam group SpamHaus and the ISP, we were able to receive access to files from the SpamThru control server. We have analyzed the files, and in this report we will look at some of the statistics and interesting finds.
SpamThru operates in a limited peer-to-peer capacity, but all bots report to a central control server. The bots are segmented into different server ports, determined by which variant of the trojan is installed. The bots are further segmented into peer groups of no more than 512 bots, keeping the overhead involved in exchanging information about other peers to a minimum. In the following graph, the total count as recorded by the control server is shown for each control port.
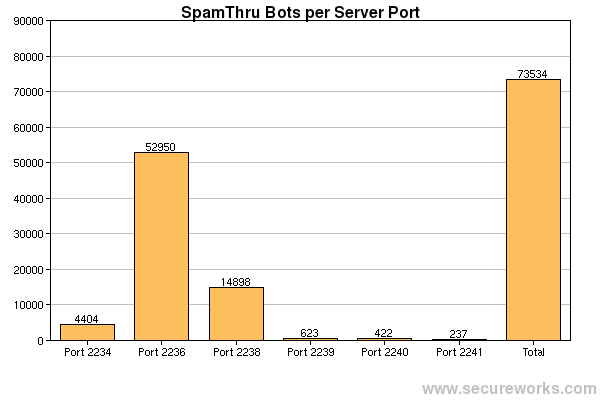
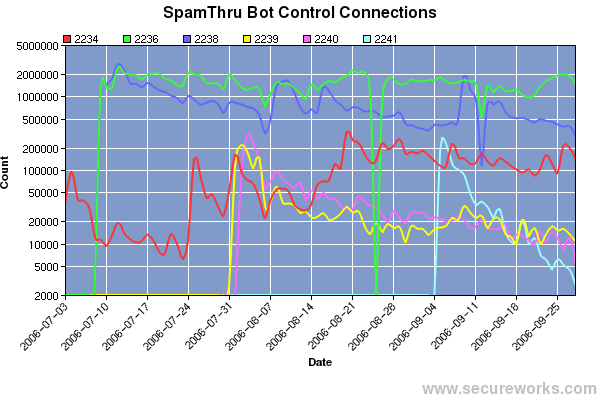
In the chart below, we can see the number of connections each control port received each day from the bots. The 2236 and 2238 variants gained a great deal more infected users than any of the other variants, sometimes bringing up to 3 million connections to the control server a day. Frequent connections are necessary to ensure that the information about the other peers is not stale, making it easier to recover in case the control server goes down.
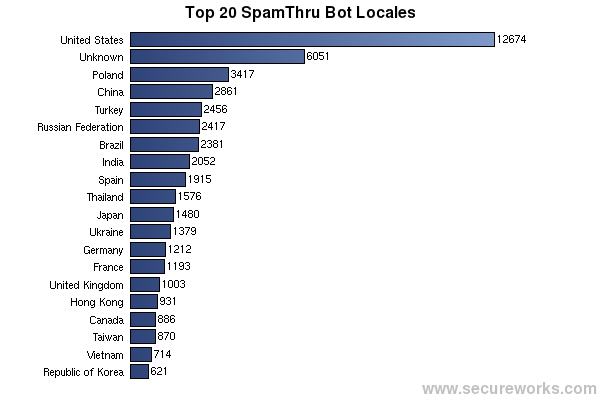
The SpamThru controller keeps statistics on the country of origin of all bots in the botnet. We can see from the graph below that, although the U.S. has the highest number of infections, bot distribution is not limited to any particular country. All-in-all, computers in 166 countries are part of the SpamThru botnet.
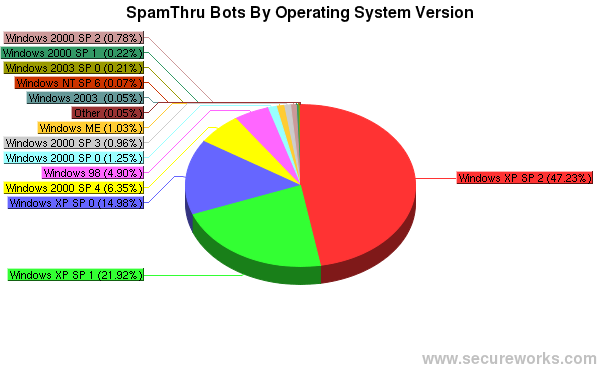
The SpamThru controller also keeps statistics on what version of Windows each infected client is running, down to the service pack level. In the chart below, XP SP2 dominates the makeup of the botnet, indicating that even fairly up-to-date systems are still falling prey to attacks.
The SpamThru bot has the capability to scan the system for other malware using a pirated copy of Kaspersky Anti-Virus. The scanning generates a report which may or may not be uploaded to the control server. In the reports that were sent, we can see a list of infected files along with the name of the detected malware. Overall, 3863 different named malware variants were found on the systems that sent scan reports back to the control server.
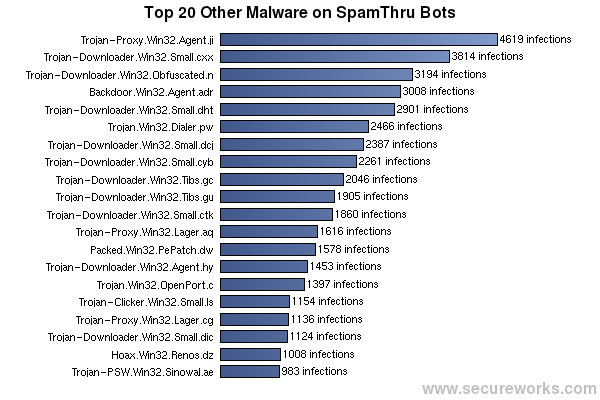
The names of infected files include the entire path to the file on the user's system. Since a large number of viruses and trojans utilize the user's temporary directory (under C:\Documents and Settings\[USERNAME]\Local Settings\Temp) as a drop point, the victim's username can be sometimes be seen in the path to the file. In many cases, this may even be the user's full name. In the image below, one such list is shown, where the victim's username is "PUBLIC SAFETY".
The SpamThru bots are also capable of using a list of proxy servers maintained by the controller in order to evade blacklisting of the bot IP addresses by anti-spam services. In this way, SpamThru acts as massive distributed engine for sending spam, but without the cost of maintaining static servers. Total spam capacity is fairly high - with 73,000 bots, given an average SMTP transaction time of 5 seconds, the botnet is theoretically capable of sending a billion spams in a single day. This number assumes one recipient per message, however in reality, most spams are delivered in a single message with multiple recipients at the same domain, so the actual number of separate spams landing in different inboxes could be even higher, assuming the spammer possesses that many email addresses.
The SpamThru spammer has general lists of millions of email addresses. In fact, one executable (detected by KAV as Backdoor.Win32.Agent.ail) that was forcibly installed via the SpamThru bot remote-control mechanism was specifically designed to harvest email addresses from the hard drives of the infected systems - giving the spammer the ability to reach individuals who have never published their email address online or given it to anyone other than personal contacts.
It also appears the spammer also made an effort to obtain more targeted lists of email addresses, by hacking into smaller investment news websites and other e-businesses and downloading their user databases. This is likely due to the fact that pump-and-dump stock spam seems to be a primary motive of the botnet.
In the image below, we can see the result of one such hack, in one of the files found on the control server. In this case, the MySQL database of an online shop appears to have been downloaded using a tool called r57shell. We know this was done in order to extract email addresses, since a file containing just the email addresses from the MySQL dump was found in the same directory.
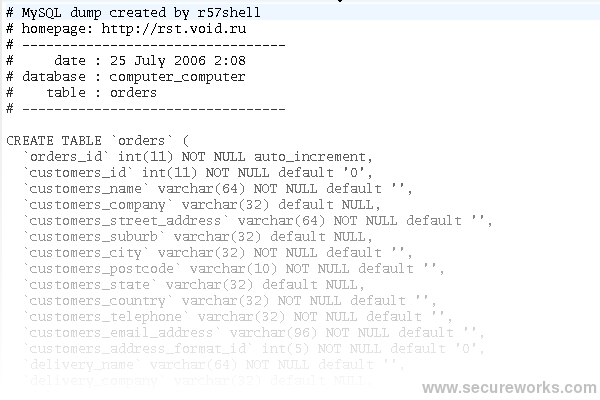
r57shell is a PHP script created by a Russian hacking group, designed to be uploaded to a vulnerable website or injected via PHP remote-file "includes", a notorious security flaw in many web applications. It gives the hacker the ability to do download/upload files, create a backdoor listener, send email, bounce a connection to another server, or administer a MySQL database, all through a simple web interface.

Based on filenames and text found in the spammer's source code, we can conclude that SpamThru is operated by one or more Russians. It seems they are not interested in a wide variety of spam, but tend to stick to a particular model of pump-and-dump stock and penis enlargement spam, perhaps because it is the most profitable. Clearly they are not concerned with the criminality of their endeavors, which is probably because Russia is not well known for prosecuting spammers or virus writers. Because of these factors and the peer-to-peer nature of the SpamThru botnet, it is likely we will continue to see this spam operation continue for a long time to come.